Up until the late 1990s, many people naively thought microwaves cooked food by making them bomb in seconds, everyone invisibly willed the internet to be as fast as it is now, and data transmission was thought of as a manual process. Data transmission is a core function of the modern day networks, active or passive, whether they serve a corporate infrastructures or an individual’s home setup. Central to every data transfer device or of every system is a computer network switch – an integral, yet often underappreciated , component of computer networking. But what is the key difference between a switch, routers, and hubs? What is its primary purpose, and why is it important to ensure the data flows seamlessly? In this context, the term “switches” will be expanded to include network switches, and their underlying features will be evaluated with other hardware components of switching, along with the vital role they play in bringing data to the end users. For industry practitioners, technology interested, and people with the basic inquisitive nature, this article strives to explain how, and what are the most critical things to note on network switches.
Table of Contents
ToggleHow Does a Network Switch Work?
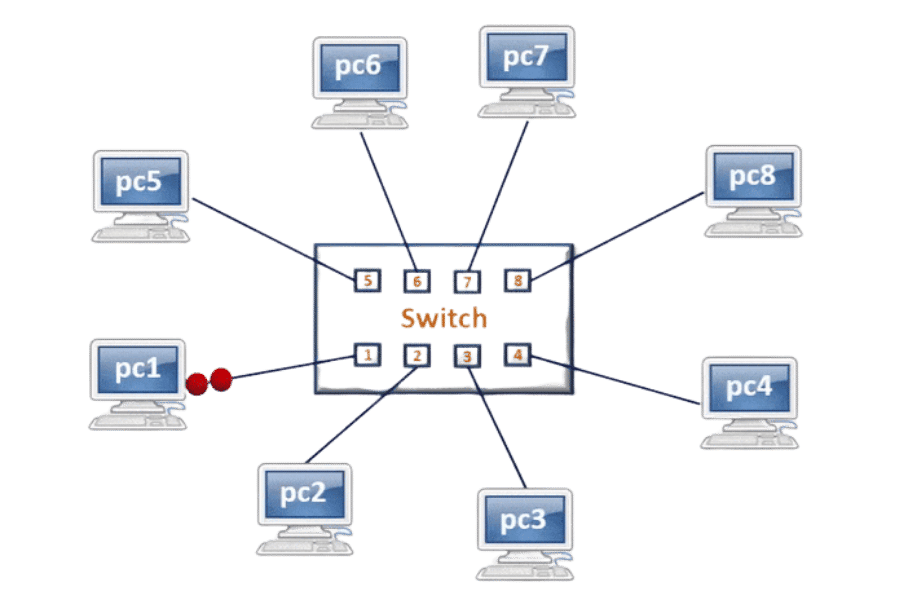
What is a Switch and How Does it Operate?
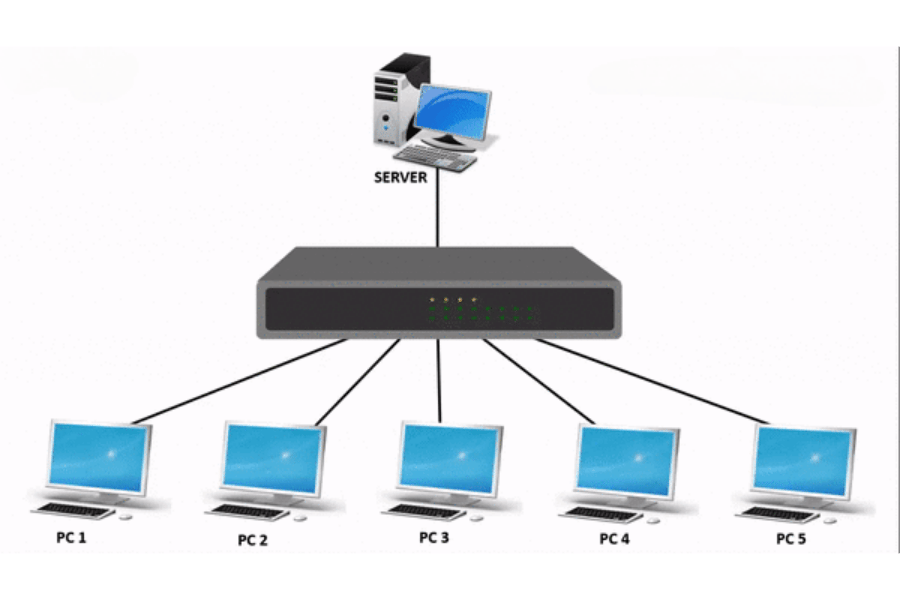
Devices within a local area network (LAN) can be connected/communicated to efficiently by the network switches. The switch handles data, and stores it, processes it, and then sends it to the intended receiving device. There is a distinction between a hub and a switch, which is, with a hub, all data is sent to any device that is connected, while a switch targets data specifically to the appropriate device using its MAC (Media Access Control) address. This assisted way of data transfer reduces network traffic along with improving performance, making network switches very important in modern LAN environments.
How Does a Network Switch Forward Data?
Using packet switching, a network switch manages to forward data. After a data packet reaches a network switch, the switch looks at the packet’s header to recognize its destination MAC address. This process tells it how a network switch operates. This is made possible by the switch’s MAC address table which correlates device MAC addresses to particular ports of the switch. If the destination MAC address is within the table, the switch sends the data packet to the proper port which guarantees efficient delivery instead of broadcasting it to all connected devices.
Modern switches also incorporate VLANs (Virtual Local Area Networks) as well as QoS (Quality of Service) features. These Advanced features allow for better segmentation of the network traffic with improved security and reduced network congestion. Different nationally recognized types of traffic like voice over ip and streaming video are ensured quality and reliability even during congested hours of the network use.
Statistics further validate the benefits of network switches. For example, a Cisco study found that employing switches with Layer 3 capabilities has the potential to cut down latency in enterprise networks by as much as 80%, while accommodating concurrent connections on sprawling infrastructures. Moreover, the adoption of modern switches with Power over Ethernet (PoE) technology enables easier deployments as devices like IP cameras and access points can now be powered and fed data through a single Ethernet cable.
This purposeful and rapid data forwarding process makes switches fundamental for low latency and highly scalable connectivity in high performance networks, both small and large structures.
The Role of MAC Address in Switch Functionality:
Switches identify and route datagrams with the use of MAC (Media Access Control) addresses. Every device that connects to a network is given a MAC address which the switch saves in a MAC address table. This table relates MAC addresses to ports, allowing switches to minimize broadcast while ensuring the data is properly fetched. The use of MAC addresses allows network switches to optimize communication within the network at a more accurate and secure scale.
What Are The Types Of Switches In Networking?
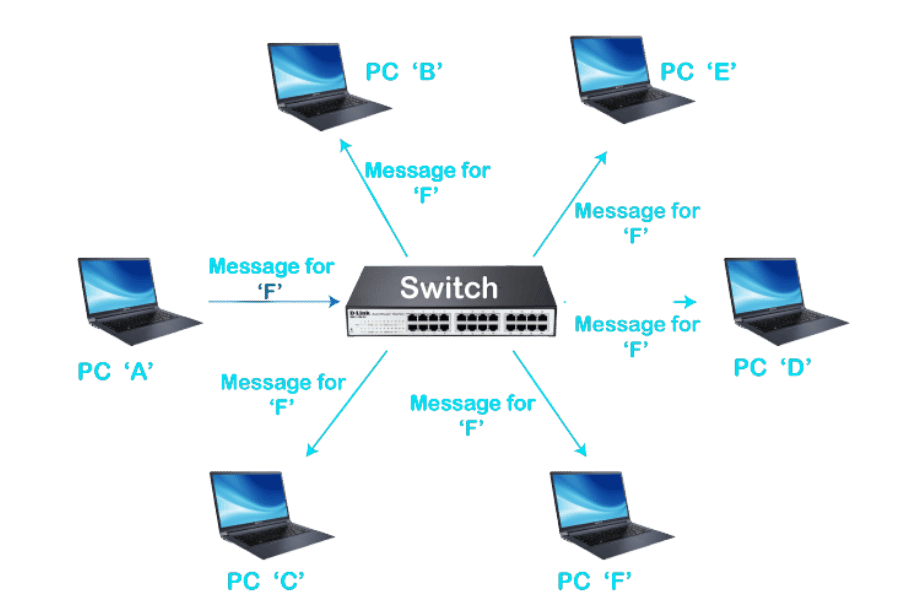
Managed Switch and Unmanaged Switch Explored
Managed Switch: With a managed switch, users gain a higher level of control over the network in which they operate. It gives administrators the power to modify configurations such as VLANs, QoS, and port speed to provide more customization options and enhance the security of the network. These switches work best in larger and more complex networks where monitoring, troubleshooting, and optimization is needed.
Unmanaged Switch: An unmanaged switch is practically the opposite of a managed switch, as it works better with a plug-and-play model that needs no prior configurations. This switch connects the device to a network, and automatically transfers data without supervision. These switches are better-used placed in small networks or more casual environments where supervision is minimal.
What Is A Layer 3 Switch?
Layer 3 switches function as high performance switches that act as a mixture between a layer two switch, and a router since it has the ability to switch and route. Layer three of the OSI model uses Layer 3 switches in a more complex way, since they are needed to route between VLANs and perform higher order functions. Unlike traditional two-layer switches, which only perform the function of forwarding packets depending on MAC addresses, layer three switches now use the IP address of the data packet to ascertain what route the data is best suited to enable all network cells to function in harmony.
Layer 3 switches are frequently used in businesses that need fast data transfer and low latency. Many modern Layer 3 switches feature support for static and dynamic routing protocols like OSPF and BGP, as well as multicast routing and QoS for traffic prioritization. Also, they are more scalable than traditional Layer 3 switches in complex and larger networks.
Recent benchmarks suggest that layer 3 switches can now process millions of packets per second (PPS), surpassing traditional routers in performance. Like other types of Layer 3 switches, these devices feature hardware-based switching, which significantly reduces delays, making the data speedier. Such devices are gaining popularity in data centers, campus networks, and enterprises for integration into the existing systems to eliminate bottlenecks, streamline network operations, and increase efficiency.
Difference Between a Switch and a Router
In Communication Technology, a switch and a router are used within a system described in a network. Accordingly, according to my understanding, a switch’s fundamental function is in Layer 2 of the OSI model, where it enables the forwarding of data within a single network by means of MAC addresses. In contrast, a router works at Layer 3 and is responsible for the interconnection of disparate networks, as well as the forwarding of information among them using IP addresses, as opposed to a switch confined to a LAN for a single network. A switch is particularly efficient in controlling the internal traffic problems of a network by keeping internal routes open. And a router makes a decision as to which route to take in order to obtain the information in a network guaranteeing connectivity and optimum data routing. The purpose of each device is fundamentally different but in them working together gives rise to seamless integration in modern networking environments.
Where in a network is a switch used?
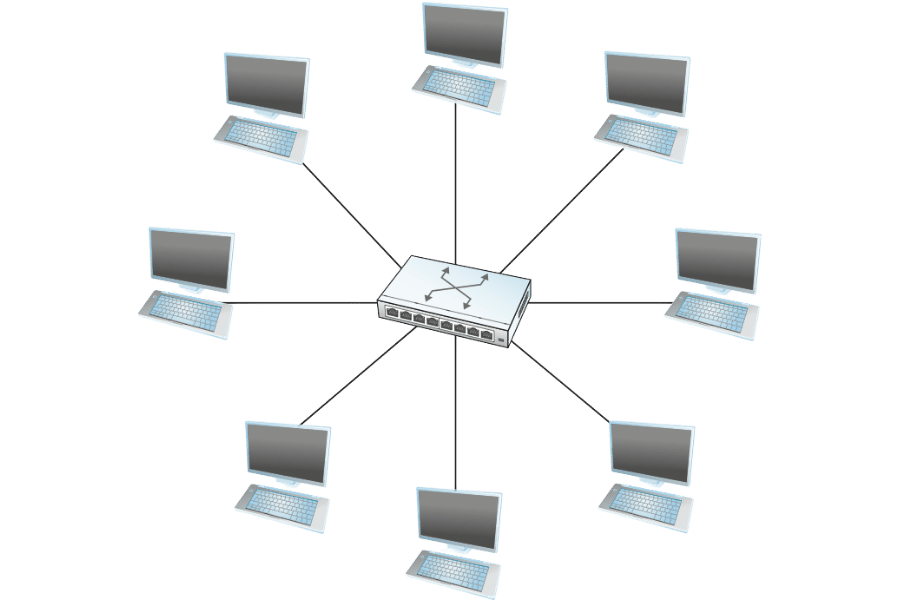
Connecting Devices in a Local Area Network
In a Local Area Network (LAN), switches connect multiple devices like servers, printers and computers so they can communicate with one another. They act as core hubs that control data traffic – information is sent directly to the relevant device so there is no need to broadcast it to all other devices. This enhances network speed, minimizes congestion, and enables dependable and secure communication between connected devices.
Role of a Switch in an Enterprise Network
Switches greatly enhance modern enterprise networks by being the fundamental components for connectivity and proficient data management. Inside an enterprise, switches facilitate the interconnection of numerous devices such as servers, workstations, access points, and IoT devices to create a well defined and scalable network infrastructure. They utilize MAC (Media Access Control) addresses to direct information to the right device which increases efficiency and decreases traffic.
An advanced performance managed switch is important for VLAN segmentation, QoS, and network redundancy. VLANs create network segments to restrict network traffic and increase security. QoS incorporates latency-sensitive traffic such as VoIP and video calls. In the computer networking industry, switches are also responsible for making resilient networks through link aggregation, TAG, and redundant fallback protocols such as STP, which stops loops in a network that cause crashing and also allows for smooth functioning when a link or device stops working.
Research shows that many organizations are relying more on enterprise switches, with a $35.8 billion global spending on Ethernet switches in 2022 already showing the need of increasing network infrastructure. Moreover, cloud-enabled applications and hybrid working have shifted the focus on switches with 10GbE and 40GbE speeds, which form the baseline for a range of applications that require high bandwidth and extensive data transfer.
All in all, enterprise switches are not just an addition to the network; they represent a substantial leap in the performance, security, and scalability of an organization’s digital infrastructure and connectivity.
Connecting Devices within a Network Using Network Switches
A switch identifies the packets data using its destination MAC address and reduces traffic to the intended recipient alone. This function consumes a small amount of time since only the user data portion of the frame need be processed. Once the data is processed, a switch, which is layer 2 device, forwards the data to the relevant port on the switch.
The Switch includes a MAC address table containing the MAC address of devices that connect to the Switch. In this way, when a device sends a data frame to the switch for the first time the switch learns the device MAC address, stores it in its table and enables communications without collisions within a LAN.
With the incorporation of routing functionality, advanced switches like Layer 3 switches can do much more. These switches allow for the transfer of data between various VLANs, or subnets, so complete data transfer can be achieved within large, complex networks. Network switches help minimize congestion and optimize data flow, which is critical to the performance and reliability of modern network infrastructures.
Choosing an Ethernet Switch: Things to Look At
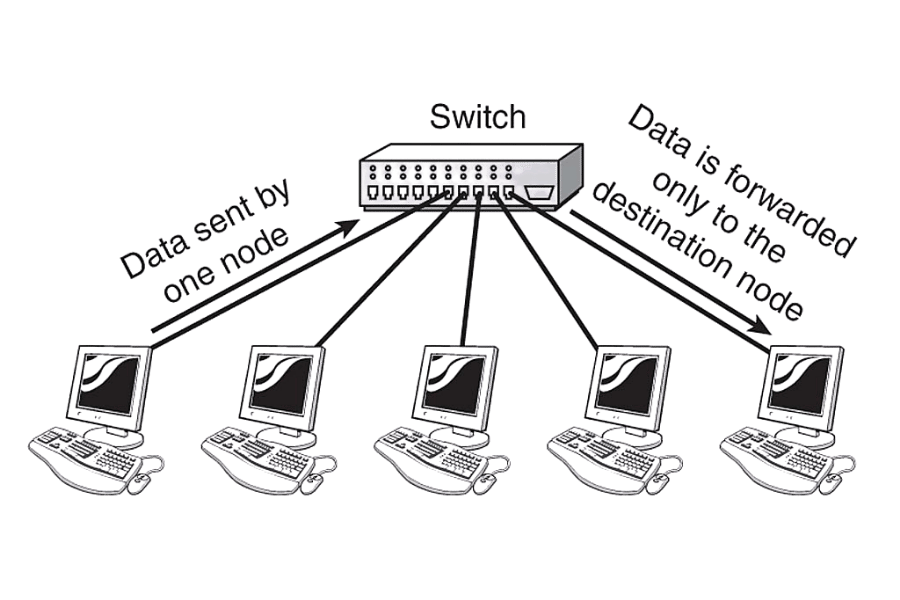
Things that Affect Network Performance
- Number of Ports and Their Speed: The device must have the required number of ports that not only fit the current devices, but also future devices. Switches that are capable of speeds at Gigabit or above ought to be purchased for quick data transfer.
- Managed/Unmanaged switches: If the network requires more sophisticated features like VLANs or prioritizing certain traffic, a managed switch would be suitable. For less complex networks, unmanaged switches ought to do the job.
- Power over Ethernet: Should the IP cameras and phones at your network need power through the Ethernet cable, then you should opt for switches with PoE capabilities.
- Expansion Capability: Assess whether the switch can accept network growth requirements of additional ports and bigger bandwidth.
- Brand Trust: To ensure reliability and reduced downtime due to hardware failures, opt for reputable manufacturers switches.
- Cost of Operation: Procure switches that consume less energy as this will help reduce operational expenses.
Considering these aspects will aid with selecting an Ethernet switch that will meet the performance requirements of the network.
Significance Of Pendant On Network Devices Using Power Over Ethernet Facility
With Power over Ethernet, one can use a single Ethernet cable to install both the power and data in a network device. This reduces the need to have a power supply from every workstation, thus reducing the clutter and overall installation costs. It is very useful for devices like IP cameras, wireless access points, or VoIP phones since these devices can freely be placed away from power outlets. Furthermore, PoE can remotely monitor and control the powered devices which improve the network efficiency and management. Networks and other device configurations will benefit from the supplementary versatility because without the pendant, operations become decreased. Thus, it is clear that the use of Power over Ethernet gives networks streamlined operations together with improved deployment versatility.
In Depth Look At Switch Ports And Their Network Connections
Switch ports are the essential sockets in which different devices can be connected in a network to allow data exchange between them. They are added on the switches for computers and servers to allow easy connection to the already existing devices. Network connections made through switch ports allow the devices to be more productive as they communicate with each other along with sending and receiving information from the global network including the internet. To make the functionality of switches superior to the others, these devices should contain ports with different speed capabilities (1 Gbps or 10 Gbps) that cater to the multitude of network needs.And that’s why managing those switch ports is vital if you want your network working properly and efficiently.
How do switches impact infrastructure of a network?
Heightening the Performance of a Network through Switching
The careful use of network switches greatly improves the network’s performance by easing congestion and enhancing data flow. Switches divide networks into smaller, easier to manage units, which allows devices to communicate without any interference. Switches also have QoS (Quality of Service) features, which enable them to funnel critical traffic for smooth operation of high-performance applications. Furthermore, switches with higher port speeds and modern protocol support can help accommodate increasing bandwidth requirements. Ongoing user monitoring and configuration of switches is necessary to achieve optimal network infrastructure performance, stability, and security.
Streamlining Network Congestion with Switch Deployment
By segmenting traffic, switch deployment helps eliminate unnecessary congestion that ultimately slows down device communicaton within a given network. Switches facilitate better device communication by intelligent packet forwarding to certain devices within a network. Such advanced techniques minimize broadcasting to the entire network which drastically eases collisions of devices trying to communicate simultaneously. This approach optimizes traffic and ensures broader slits for Scalability. This is guaranteed by deploying switches with sufficient port capacity and by using VLANs (Virtual Local Area Networks). Such strategies minimize bandwidth utilization while maximizing network performance.
How Switches Function in The Administration of A Network
Efficient data transfer and network operations are simplified with the use of switches, thus making them important tools in network management. Switches are central connection devices, therefore, they serve the purpose ofgets interconnecting various devices and receiving information from each data source and transfers it to the required subjects. Through traffic segmentation, network congestion is minimized and network switch devices enhance efficiency. Even more, they improve security by supporting network policies such as isolation communication and access control. Modernized switches can also include traffic prioritization, network health monitoring, and advanced configuration support making those switches critical parts in reliable and scalable networks.
Frequently Asked Questions (FAQ)
Q: Explain what a network switch is and compare it with a hub.
A: A network switch is a central point of connection for various devices in a network. While a hub sends information to all devices, a switch only sends data to the intended recipient, which results in security and efficiency in the network.
Q: What type of network does a switch typically operate in?
A: A network switch mainly functions in local area networks (LANs). In Ethernet based LANs, it is an important component to connect different devices such as computers and printers to a single switch or to multiple switches across larger networks.
Q: How does a network switch manage IP addresses?
A: Network switches work using Layer 2 of the OSI model. They do not work with IP addresses directly, but instead they forward the data packets using MAC addresses. Some switches have limited Layer 3 capabilities, which means they can also use IP addresses to route traffic in certain situations.
Q: What is a stackable switch and how does it work in large networks?
A: Stackable switches are those devices that can form a single unit when connected to similar devices. That is why it is easier to manage and scale the stack of switches which is particularly useful in large networks or data center networks.
Q: In what ways a switch can be utilized for network monitoring?
A: Almost all modern switches have capabilities such as port mirroring and SNMP, which allow for network monitoring. With port mirroring, information from one or more ports can be sent to another port for further examination. In contrast, SNMP permits a network administrator to observe and control the network’s general operations and health and proactively resolve any problems while collecting data in the process.
Q: What is the contribution of network interface card (NIC) towards a single switch user?
A: Devices with networks switches must have a Network Interface Card (NIC). It serves as the point of contact and as the communication protocols with the device. The network interface card has a distinct MAC address embedded into it which enables the switch to identify the device and route data to and from the device appropriately.
Reference Sources
1. Hipernetch: High-Performance FPGA Network Switch
- Authors: Philippos Papaphilippou et al.
- Journal: ACM Transactions on Reconfigurable Technology and Systems
- Publication Date: March 31, 2022
- Key Findings:
- The document introduces Hipernetch which is a new FPGA based design for switching networks with high bandwidths.
- It supersedes typical crossbar structures with a “combined parallel round-robin arbiter” that improves pipeline performance and decreases delays.
- The implementation obtains throughput exceeding 100 Gbps per port for switches of up to 16 ports.
- Methodology:
- The authors created the architecture of Hipernetch and analyzed the performance concerning traditional switching architectures revealing the advantages in throughput and latency.
Citation: (Papaphilippou et al., 2022, p. 3:1-3:31)
2. Evolving Switch Architecture toward Accommodating In-Network Intelligence
- Authors: Shuangwu Chen et al.
- Journal: IEEE Communications Magazine
- Publication Date: January 1, 2020
- Key Findings:
- Here we are focusing on the improvements made to the switch architecture through the incorporation of an intelligence plane which enables in-network decision making as well as processing.
- The suggested design enables the provision of robust performance and high application throughput, allowing AI to be integrated easily into network operations.
- Methodology:
- The authors offer a conceptual framework for the evolved switch architecture and demonstrate its deployment in a campus network. The implementation is verified by experimental results pertaining to its features.
Citation: (Chen et al., 2020, pp. 33–39)
3. Time-Triggered Switch-Memory-Switch Architecture for Time-Sensitive Networking Switches
- Authors: Zonghui Li et al.
- Journal: IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems
- Publication Date: January 1, 2020
- Key Findings:
- The document presents the time-terminated switch-memory-switch (SMS) architecture aimed at achieving low memory footprint in time sensitive networking (TSN).
- This permits the static scheduling of memory allocation, which enhances both resource utilization and fault tolerance.
- Methodology:
- The authors implemented the SMS framework and executed simulations to test its effectiveness with regards to memory usage and scheduling efficiency.
Citation: (Li et al., 2020, pp. 185–198)
4. Incremental Deployment of Programmable Switches for Network-wide Heavy-hitter Detection
- Authors: Damu Ding et al.
- Journal: 2019 IEEE Conference on Network Softwarization
- Publication Date: June 1, 2019
- Key Findings:
- This document seeks to introduce a method for the gradual implementation of programmable switches in an Internet Service Provider network for the purposes of monitoring unique network flows.
- This method reduces the amount of information needed from the data plane while ensuring precise detection of heavy flows.
- Methodology:
- The writers designed two Integer Linear Programming (ILP) models for the allocation of programmable switches and verified their method with simulations on actual ISP topologies.
Citation: (Ding et al., 2019, pp. 160–168)
5. Poseidon: Mitigating Volumetric DDoS Attacks with Programmable Switches
- Authors: Menghao Zhang et al.
- Journal: Proceedings 2020 Network and Distributed System Security Symposium
- Publication Date: 2020
- Key Findings:
- The paper reports on Poseidon which uses programmable switches to protect against volumetric DDoS assaults.
- It lets users define modular defenсe strategies that can be flexibly modified in correlation with the developing attack patterns.
- Methodology:
- The authors deployed Poseidon on programmable switches and performed testing to validate its efficiency in DDoS attack detection and mitigation with minimal resource expenditure, guaranteeing steady traffic through the network.
Citation: (Zhang et al., 2020)
Related Products:
-
 S3100-48T2Q4X, 48-Port Ethernet Switch, 48x 10/100/1000/2500/10G BASE-T RJ45, with 2x 40G SFP+ and 4x 1G/10G SFP+ Uplinks
$1095.00
S3100-48T2Q4X, 48-Port Ethernet Switch, 48x 10/100/1000/2500/10G BASE-T RJ45, with 2x 40G SFP+ and 4x 1G/10G SFP+ Uplinks
$1095.00
-
 S3100-24T6X-P, 24-Port Ethernet Switch L3, PoE+ Switch, 24x 10/100/1000/2500 BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$746.00
S3100-24T6X-P, 24-Port Ethernet Switch L3, PoE+ Switch, 24x 10/100/1000/2500 BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$746.00
-
 S3100-48T6X-P, 48-Port Ethernet Switch L3, PoE+ Switch, 48x 10/100/1000BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$734.00
S3100-48T6X-P, 48-Port Ethernet Switch L3, PoE+ Switch, 48x 10/100/1000BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$734.00
-
 S3100-8T4X, 8-Port Ethernet Switch L3, 8x 10/100/1000/2500/10G BASE-T RJ45 Ports, with 4x 1G/10G SFP+ Uplinks
$398.00
S3100-8T4X, 8-Port Ethernet Switch L3, 8x 10/100/1000/2500/10G BASE-T RJ45 Ports, with 4x 1G/10G SFP+ Uplinks
$398.00
-
 S3100-48T6X, 48-Port Ethernet Switch L3, 48x 10/100/1000BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$365.00
S3100-48T6X, 48-Port Ethernet Switch L3, 48x 10/100/1000BASE-T RJ45, with 6x 1G/10G SFP+ Uplinks
$365.00
-
 S2100-24T4TS-P, 24-Port Ethernet Switch L2+, PoE+ Switch, 24x 10/100/1000BASE-T RJ45, with 4x 1G RJ45/SFP Combo Uplinks
$360.00
S2100-24T4TS-P, 24-Port Ethernet Switch L2+, PoE+ Switch, 24x 10/100/1000BASE-T RJ45, with 4x 1G RJ45/SFP Combo Uplinks
$360.00
-
 S3100-16T8TS4X, 16-Port Ethernet Switch L3, 16x 10/100/1000BASE-T RJ45, with 8 x 1Gb RJ45/SFP Combo and 4 x 1Gb SFP Uplinks
$340.00
S3100-16T8TS4X, 16-Port Ethernet Switch L3, 16x 10/100/1000BASE-T RJ45, with 8 x 1Gb RJ45/SFP Combo and 4 x 1Gb SFP Uplinks
$340.00
-
 S2100-16T2S-P, 16-Port Ethernet Switch L2+, PoE+ Switch, 16x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$230.00
S2100-16T2S-P, 16-Port Ethernet Switch L2+, PoE+ Switch, 16x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$230.00
-
 S2100-24T4TS, 24-Port Ethernet Switch L2+, 24x 10/100/1000BASE-T RJ45, with 4x 1G RJ45/SFP Combo Uplinks
$148.00
S2100-24T4TS, 24-Port Ethernet Switch L2+, 24x 10/100/1000BASE-T RJ45, with 4x 1G RJ45/SFP Combo Uplinks
$148.00
-
 S2100-8T2S-P, 8-Port Ethernet Switch L2+, PoE+ Switch, 8x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$139.00
S2100-8T2S-P, 8-Port Ethernet Switch L2+, PoE+ Switch, 8x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$139.00
-
 S3100-4T2X-P, 4-Port Gigabit Ethernet Managed Switch, PoE+ Switch, 4x 10/100/1000/2500 BASE-T RJ45, with 2x 1G/10G SFP+ Uplinks
$90.00
S3100-4T2X-P, 4-Port Gigabit Ethernet Managed Switch, PoE+ Switch, 4x 10/100/1000/2500 BASE-T RJ45, with 2x 1G/10G SFP+ Uplinks
$90.00
-
 S2100-8T2S, 8-Port Ethernet Switch L2+, 8x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$71.00
S2100-8T2S, 8-Port Ethernet Switch L2+, 8x 10/100/1000BASE-T RJ45, with 2x 1G SFP Uplinks
$71.00












