In the present-day Internet world, smooth data transfer and communication are paramount. Ethernet network switches come into play at corners of the world. Assist devices to the modem or the router; this equipment forms the core of modern and contemporary networks, Providing a firm base to businesses, households, and enterprises, achieving faster speeds with efficiency and connectivity to the maximum. Seeking to get a small office set up, for instance, upgrading the home net or overseeing a complex IT structure, one of the strongest features to comprehend is Ethernet switches. This guide will assist in understanding their function better, among other features, thus enabling you to maximize your network’s capabilities. It’s time to take your connectivity, communication, and achievements to the next level when innovation in desktop Ethernet has taken over.
Table of Contents
ToggleWhat is an Ethernet Switch, and How Does It Work?

An Ethernet switch is a crucial networking hardware that facilitates connection and communication with multiple devices in a local area network, also known as a LAN. These devices usually operate by sending data cables through the switched Ethernet which only forwards the data to the destined device, this further increases network efficiency by keeping the data the device is aimed for at a minimum.
Ethernet switches function on layer two of the OSI model which is known as the data link layer, the connected devices on the network are recognized through MAC addresses. This guarantees the security and accuracy of the data sent by learning and storing addresses in what is known as the forwarding table, Ethernet switches are capable of doing much more than just layer 2 switching, as some are also layer 3 switching capable. , in general Ethernet switches increase reliability and scalability of the networks.
Understanding the basics of Ethernet switches
Ethernet switches can be divided primarily into two groups in terms of their working and the supervision level allotted to them:
- Unmanaged Switches: This type comprises uncomplicated plug-and-play switches that are operated with no prior configuration. All switched devices are able to communicate with each other as these devices facilitate automatic communication forwarding. Home users and small networks that do not require much device setup install these switches into their networks.
- Managed Switches: These comprise switches that are capable of handling a greater amount of configuration with respect to the functionalities of the network. Such managed switches can perform several features such as configuring VLANs, traffic management, and other deadline modifications, to mention a few. These switches connect with corporate networks or other complex systems where a high degree of performance tuning and tailoring is required.
For different functions both serve distinctly different functions and hence, when selecting the type of switch, it’s the requirements in the particular network setting that would determine what you would need.
How Ethernet switches differ from routers
Ethernet switches and routers are very essential devices to any network that uses them but they perform different functions in this network. An Ethernet switch can connect devices operating within a local area network (LAN). It is a Layer 2 (Data Link Layer) device in the OSI Model and employs MAC addresses to switch data frames between devices in its site. Switches are a fundamental element for communication in the same network and effectively use bandwidth by ensuring information is sent to the correct target.
Routing devices, however, work on Layer 3 of the OSI model and are used to connect two or immediate networks together. Routers, unlike switches, which concentrate on local or inter-network communication, use IP addresses to send packets across various local areas and up to the internet. Routers also carry out network address translation (NAT) and Dynamic Host Configuration Protocol (DHCP) functions which allow the computers from private networks to communicate with other external networks.
The commonality emerges from their ancillary functions as routers are specialists in isolating the appropriate packet while switches optimize network performance by curtailing traffic on the network. TACIT permits data traffic only, while switches determine data traffic patterns. OSPF and BGP are aided in packet determination via routing tables.
The disparities in capacity and speed within said devices can be observed with performance data. Enterprise Ethernet versions with over 48 ports are catered for 100 Gbps and above speeds which makes them suitable for efficient data centers. Routers, on the other hand, are primarily used for controlling internet traffic and assisting with WAN integration, as they have limited ports but advanced traffic routing.
Allocating resources and maximizing performance is catered effectively due to planning made while considering the role of multiple devices within a network structure. Routers are paired with switches to facilitate secure and smooth communication networks regardless of the network environment.
The role of MAC addresses in switch operation
MAC (Media Access Control) address systems allow devices to send packets over a local area network (LAN) without overlapping with any other system, making network switches’ performance seamless. Simply, a MAC address can be defined as a 48-bit hexadecimal code assigned to a device’s Network Interface Card (NIC). These addresses are essential for switches, security, and intelligence to form and adjust networks’ MAC address table that links devices connected to the switch to its various ports.
When a switch receives a data frame, it evaluates the frame’s source MAC address and records it in the MAC address table with a corresponding port. Simultaneously, the switch retrieves the destination MAC address and cross references it to the MAC address table to find a port to send the frame to. If the destination MAC address does not exist on the table, the switch resorts to flooding, in which the frame is sent across all ports except the port it was originally received.
In order to increase performance, switches modify the MAC address table with a certain frequency and delete its contents after they have remained idle for a set period. This helps retain space and simplifies computation by ensuring that the tables are not outdated. More advanced switches incorporate such functions as VLANs (Virtual Local Area Networks) and support for dynamic routing protocols in addition to using MAC addresses as a security measure in multi-user environments, which further enhances MAC address use.
In the context of modern advancements in networking technologies and switches, it’s now possible to make MAC tables larger with even more devices connected to high-density networks. For example, many vendor enterprise switches have a MAC address entry number of 128,000 or so, which, in essence, enables OC to reach greater heights in data-hungry environments like campuses and data centers. MAC addresses are an indispensable part of switch operation characteristics which ensure stability and scalability on LANs.
Types of Ethernet Switches: Which One is Right for Your Network?
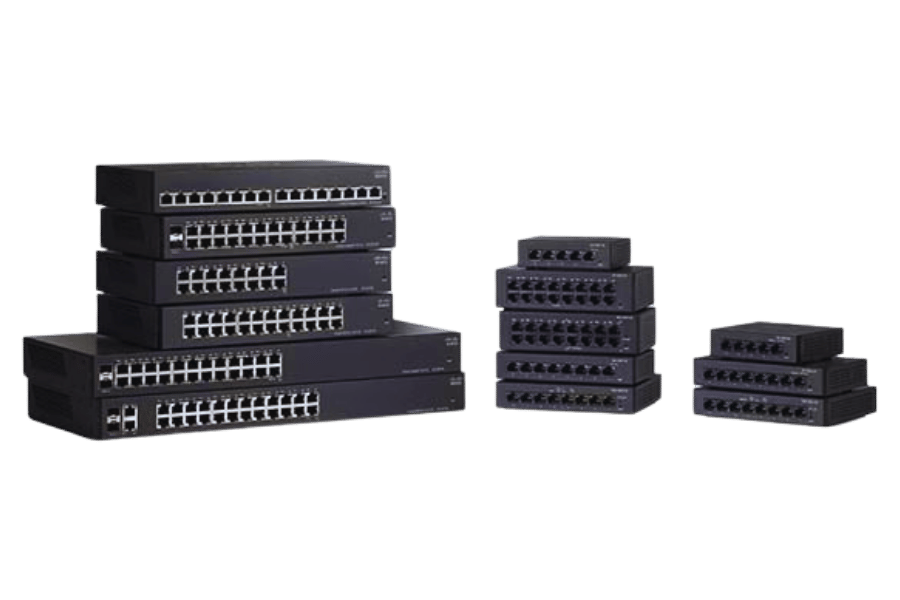
Managed vs. unmanaged switches: Pros and cons
Managed and unmanaged Ethernet switches differ in a few aspects, which can be crucial when considering their effect on a network’s performance, scalability, or control. Understanding these differences is essential as well while selecting between the two classes of switches.
Unmanaged Switch
Unmanaged switches are appropriately named as they do not require any management and serve the purpose of dwelling in a ‘plug and go’ status. They are very basic, as advanced functionality is abandoned and their cost is lowered. However, a price drop means offering limited functions meaning they cannot be used on medium to bigger networks, instead they can be used at home offices or small offices. Certain features, such as VLANs and QoS, are weak or missing, and as a result, monitoring or even troubleshooting is rendered useless. Their minimal configuration leaves them inflexible, however, the fact they do plug and go facilitates easy deployment to an extent.
Pros:
- Economic and user friendly
- No previous knowledge of area networking is required
- Suitable for small to medium networks with lower bandwidth needs.
Cons:
- Advanced traffic analysis and performance management is underdeveloped
- Features like access control and encryption are nonexistent
- It is hard to scale and may not be great for business-level applications
Managed Switches
Unlike the other switches, managed switches offer great customization, monitoring, and traffic management for more complicated network topologies. They enable network admins to set configurations on the individual ports and bundle them to enable more security features and other processes, such as traffic prioritization. Managed switches are popular within businesses and data centers, where uptime and performance is paramount. Layer 3 routing, SNMP monitoring, redundancy protocols, and other network diagnostic tools are advanced features that increase the dependability of the mesh. This elevated versatility requires advanced responsibility as well as a great financial investment. However, managed switches also boost revenue and considerably improve cash flow and profitability.
Pros:
- Performance is enhanced through VLAN and QoS support.
- More access control options lead to stronger security within the mesh.
Cons:
- Costly than unmanaged switches
- Far more skilled network management is required
- There’s a configuration complexity with scale
While selecting the best switch for the network, take into account your use case, resources, growth needs, and required amount of control and security strength. An unmanaged switch will work for smaller businesses, or this is not a critical application. Otherwise, it is advisable to use managed switches for larger and constantly changing ecosystems as they provide adequate depth and capacity.
PoE switches: Powering devices through Ethernet.
Power over Ethernet switches allows the connection of devices for data and electrical power using a single Ethernet cable. Such a feature removes the need for an additional supply of power or any extra cabling to be installed, which, in effect, saves time and cost. Commonly, PoE switches supply power to devices such as IP cameras, VoIP phones, wireless access points, and other similar devices. Industry standards, including IEEE standards 802.3af, 802.3at, and 802.3bt, guide PoE switching devices’ operation and power supply. In this respect, PoE switches allow companies to maintain consistency in the network’s physical structure while enhancing the location of the devices.
Gigabit Ethernet switches for high-speed connectivity.
Gigabit Ethernet switch is capable of providing the required connectivity at high speeds, with a data transfer rate of 1 Gbps per port. Such switches are crucial in bandwidth-hungry applications such as video conferencing, massive data transfer, or services hosted on the cloud. They facilitate device intercommunication without bottlenecking the network. A gigabit switch is widely employed in both corporate and small-scale business environments, and it can be deployed with prior existing Ethernet standards, making it easy to implement within the network systems or even the latest ones. Their superior performance ensures that they have high scalability, which makes them perfect for an expanding network that requires fast and efficient connectivity.
How to Choose the Best Ethernet Switch for Your Home or Office

Determining the number of ports you need
While determining the total number of ports needed in the switch, consider the number of computers, printers, smart televisions, gaming consoles, or any other Ethernet devices you may require for the network. It is additionally prudent to factor in a few additional ports for any future expansion, owing to the fact that devices presently to be connected may be expected to increase in number. Such an example would be if it is a home network hub and five devices need to be connected to it, then selecting the eight port switch will work quite well since it allows for expansion. Always make sure that the selected switch is suitable for at least your current state of the network as well as your expected requirements.
Considering speed and bandwidth requirements
When comparing Ethernet switches, it is also important to consider speed and bandwidth features to avoid poor network performance. An Ethernet switch has a rating of speed. For example, Fast Ethernet has 100 Mbps, Gigabit Ethernet has 1 Gbps, and finally, 10 10-gigabit Ethernet has 10 Gbps. Currently, the vast majority of households and smaller firms require only a Gigabit Ethernet switch since it allows for high-speed internet connections and applications such as cloud-based services and 4K streaming.
The overall bandwidth of the network is significantly influenced by bandwidth. A gigabit ethernet switch is typically rated to have 1 Gbps bandwidth per port, although the bandwidth of the backplane determines a limitation. This specifies that a gigabit eight-port switch would ideally require a switching capacity of 16 Gbps, which equates to 1 Gbps Full duplex per port.
The type of devices and applications you have should also be considered and how much bandwidth each of them requires. While playing video games or making video calls and transferring large files require a stable high-bandwidth TCP/IP or other bandwidth does not have such demands, and web browsing or sending emails does not require that high bandwidth. Being aware of those requirements enables you to select an Ethernet switch that guarantees the smooth operation of your network during the busiest hours.
Evaluating additional features like VLANs and QoS
In my analysis of extra options that can be integrated into the algorithm such as VLANs and QoS, I emphasize how these capabilities can improve the performance of the network and its control. VLANs allow me to efficiently divide the traffic hence enhancing security and reducing traffic bottlenecks. At the same time, QoS allows me to prioritize critical traffic such as video conferences or VoIP to ensure reliable performance even at peak times. Both features complement perfectly the optimization of the network for specific requirements.
Setting Up and Configuring Your Ethernet Switch

Step-by-step guide to connecting devices
CHOOSE THE DESIRED POSITION
I start by placing the Ethernet switch in a well-ventilated and secure cabinet, which is proximate to both the location of the devices I intend to connect. This goes a long way in reducing the length of the cables and ensuring that good performance is maintained.
SWITCH THE DEVICE ON
I now connect the switch to an appropriate power source through the power adapter provided. I ensure the switch turns on successfully by looking at the indicator lights.
USING ETHERNET CABLES, CONNECT DEVICES
I connect each device to the switch via Ethernet cables, with one end connected to the device’s network and the other to an unoccupied port on the switch.
CHECK IF THE DEVICE IS CONNECTED
After the connection has been made, I look for the indicator lights on the switch associated with each of the ports. These lights are used as indicators to show whether the connection has been successfully achieved, as those lights show when the connection is on or flashing.
TESTING NETWORK FUNCTIONALITY
Lastly, I test to see whether all the devices that are now interconnected are able to communicate with each other over the network. Usually, I do this by attempting to access any of the shared resources or the internet, based on how the network is organized.
Configuring VLANs for network segmentation
Ethernet Local Area Networks function by enabling network managers to appreciate that a single Ethernet LAN can be broken into multiple logical LANs for the purpose of security or geographical dispersion. Hence, Ethernet VLANs enhance traffic management by improving security and promoting network performance.
How Many Steps Can I Follow To Set Up My Ethernet LANs?
Here are some guidelines for anyone who is trying to appreciate how Ethernet VLANs work.
Gain Access to the Switch Interface
Evidently, this can be achieved by accessing the command line interface or the web management console over the network.
Create VLANs
From appropriate Layer 3 devices, it is possible to create VLANs by assigning IDs to each VLAN. Such an ID can simply be understood as a number between 1 and 4094 under IEEE802.1Q. For instance, VLAN ID 10 can be assigned to employee devices, VLAN ID 20 for guest access, and VLAN ID 30 to VoIP devices.
Assign Ports to VLANs
Ethernet LAN is able to carry wired traffic and it is possible to define the switch ports for each of the VLANs so as to facilitate communication across the different set of ports. Each port can be configured to operate in either the access or the trunk mode, that is, a single VLAN is assigned to the given port or multiple VLANs are assigned coupled with tagging. An example would be switching ports 1-10 for VLAN ID 10 and ports 11-15 for VLAN ID 20.
VLAN Trunking Configuration
When configuring VLAN Trunking, make sure to enable the feature on the links between switches or between the switches and the router. There are tagging protocols, such as IEEE 802.1Q, which employ VLANs on the same link, allowing trunking.
Verification of VLAN Configuration
To confirm the VLAN setup, utilize commands or monitor tools. Ensure the relevant devices in the configured VLAN can intercommunicate with ease while traffic in between the VLANs sent over routers or Layer 3 Switches is completely absent, with an exception in cases where routing or switching is utilized.
VLANs Advantages
- Performance improvement: With the creation of VLANs, the size of the broadcast domain is reduced, which means that unwanted traffic generated will also be decreased along with more efficiency in the usage of the bandwidth.
- Increased Security: Devices can be grouped into their respective VLANs which will prevent other groups from gaining unauthorized access. For example, sensitive financial systems can operate on a restricted VLAN.
- Easier Network Management: Adding devices and relocating them becomes more straightforward, as physical re-cabling is not required should such changes to the network be necessary.
Statistical Support
Analysis of recent trends shows that businesses that integrate VLANs usually benefit as much as 30% in bandwidth usage when compared to utilization. Furthermore, VLAN set-ups reduce the scope of internal cyber attacks by 70%. By intrusions being formulated or attacked within the wider scope of VLAN, movement across the network is limited to only specific segments.
The application of VLANs is more effective when one fully grasps the network design and its traffic behavior. The correct kind of segmentation together with the monitoring and modification of the VLANs, helps in sustaining the ever growing contemporary network demands.
Optimizing switch performance for your network
In the competition of improving switch performance in a particular network setting, one must devise robust configurations and methods which can endure the rise in the traffic without degrading latency and reliability speeds. The current generation of switches comes embedded with essential tools, for instance, Quality of Service rate control (QoS), energy-efficient Ethernet ports, and port aggregation, while these features are capable of increasing network performance significantly.
1. Enable Quality of Service (QoS): By implementing QoS, network administrators are equipped with the capability to manage and type as per the user requirements the sort of critical traffic that is presented over the network, for instance, better voice performance on demand VoIP or video type conferencing. According to previous studies where QoS was efficiently implemented, there was an up to 60% reduction in the loss of data packets, which supported the majority of the real-time applications.
2. Use Port Trunking (Link Aggregation): Bandwidth capacity can be increased and potential faults can be avoided by merging a number of physical links into a single logical link. One clear example is the use of IEEE 802.3ad link aggregation during busy network operations, which can increase up to 70% bandwidth allocation.
3. Optimize Spanning Tree Protocol (STP): There are various factors that reduce the efficiency of interconnects in providing delay-free service, one being the poor configuration of the STP, which can lead to loops or cycles within the virtual network. By incorporating other options like Rapid Spanning Tree Protocol (RSTP), users can as much as quadruple the speed of the convergence time from Normal to Rapid spanning.
4. Utilize Layer 3 Switches: For networks that handle large amounts of data, layer 3 switches complete the performance by distributing routing duties from routers. These switches cut down the number of hops and increase the internal network flow, which is ideal for the environments of corporate level.
5. Be Conscious of Electricity Consumption: Switching technologies like the IEEE 802.3az that are energy efficient adjust their power consumption based on traffic needs. Energy-conserving switches can cut back electricity consumption by 50%, assisting in increasing the goal’s sustainability and decreasing operational expenditures simultaneously.
6. Schedule Regular Firmware and Security Updates: Firmware of switches that is not current can cause compatibility and vulnerability management. It is wise for network managers to develop plans for updates to ensure they contain recent features and security fixes.
By combining these strategies and tools, switches can be optimized for peak performance if they are supplemented with modern organizational needs for scalability and resilience. Proper implementation means the retention of networks in an active, effective, and safe state from immeasurable challenges.
Troubleshooting Common Ethernet Switch Issues

Dealing with connectivity problems
Whenever you experience connectivity problems with your Ethernet switches, it is advisable to follow a particular troubleshooting process strictly in order to rectify the problem in the most effective manner possible. Some of the common causes of such connectivity issues include damaged cables, erroneous switch settings, and malfunctioning of any hardware device.
- Cable Testing: Begin with inspecting the Ethernet cables for any physical damages like cuts or twisted connectors. According to statistics, 70 percent of network issues are caused by damaged or poor-quality cables. After your inspection, utilize a cable tester to make sure all the connections are working fine and the standards required for data transfer are being met.
- Configuration and Port Settings: Switch setting misconfigurations are a cause of poor or no connections on the Ethernet switches. It is important to check that all port settings, including speed and duplex configurations on the devices, are identical to one another. For instance, duplex settings that are different between the switch and the device plugged into it can cause a poor performance because of the high rate of collisions.
- Power over Ethernet (PoE): If PoE is enabled on your switch, check if the connected devices are consuming adequate power and also check if the switch is in budget of PoE. Otherwise, you can experience a loss of connectivity to certain devices due to the exceeded power budget.
- Consider Traffic Jams In Networks: Their cause is often network loops. Such storms can cloud a switch, interrupting connections. Use of its options, for example, spanning tree protocol (STP), gets rid of the problems and centers the network. Due to unusual increases in network traffic coupled with other forms of activity, notice broadcast storms and act accordingly.
- Always install the latest firmware or software for the network devices in order to secure the network and ensure proper operation of the devices in an Ethernet LAN.: If firmware or software is outdated, that device is likely to face connectivity problems. Suppose the device faces bugs or compatibility issues. In that case, there are prospective solutions and patches available, and one of the most important things which gets accomplished on a regular basis is updating the software to the new patches. Research conducted by Cisco mentions that close to 15 percent of the connectivity issues are solved by attaching the latest firmware for the router.
- Hardware Testing and Replacement: If the aforementioned procedures are ineffective, it might be useful to analyze the switch hardware. It may also be helpful to use the vendor’s built-in troubleshooting tools, Ineffective switches can be replaced with tested switches.
Following these steps, parts of the strategy can help solve connection problems. Also, portions of the network must document all configurations and problems in detail to enhance faster problem-solving in the future.
Resolving PoE-related issues
Common issues with Power over Ethernet (PoE) stem from improper power allocation, faulty cables, or device incompatibility. To overcome these issues:
- Confirm the power requirements – Ensure with the powered device that it does not exceed the PoE injector or switch. Also, make sure that appropriate power budgets are allocated with the multi-device setup.
- Examine cabling – Ensure the cables are undamaged or free of any defects. Additionally, do not use Ethernet cables below the Cat5e standard, as they do not comply with the PoE requirements.
- Assess the compatibility devices – Ensure that the Power Sourced Equipment and the PD comply with the same standard of switching such as IEEE 802.3af or 802.3at.
- Modify firmware and settings – Make amendments to the firmware of the PoE injectors or switches and confirm PoE settings.
In most cases these steps will resolve any issues being faced with the Ethernet splitter, ensuring smooth operations.
Addressing network slowdowns and bottlenecks
In striving towards the elimination of or reducing network bottlenecks or slowdowns, do the following key things:
- Examine User’s amount of bandwidth consumption – Determine whether the bandwidth on offer is capable of satisfying the consumption out there; if the usage gets close to the offering bandwidth on a continuous basis, Increase the connection.
- Modify Quality of Service (QoS) parameters – Allocate critical devices or applications to the top of a queue so that they get serviced first during busy hours.
- Traffic patterns – Employ the use of network performance tools and applications to detect abnormal devices or patterns that seem to greatly consume bandwidth. Limit or bar devices from accessing the requirements where it is applicable.
- Hardware components – Routers and other network components, such as switches, must work properly and have the latest updates or patches. Equipment suspected of being faulty or outdated must be replaced.
- Differentiate networks with high traffic – Set up different virtual local area networks, also known as VLANs and subnetworks, so that devices do not use one network alone.
The above steps, when pursued thoroughly, will lead to the identification and rectification of components responsible for poor network responsiveness and increased reliability.
Expanding Your Network: Scaling with Ethernet Switches

Daisy-chaining switches for larger networks
In considering the daisy-chaining of switches in large networks, I strive to meet the requirements of a well-coordinated topology to alleviate performance restrictions like bottlenecks and excessive delay. I daisy-chain using the uplink ports and go in the logical order so that latency is reduced to an extent. I also set up STP to avoid loops in the networks which assists in maintaining effective communication and stability in the network. This strategy enables me to increase the capacity of the network while ensuring dependability.
Integrating wireless access points with your switch
When configuring Wireless Access Points alongside my switch, I make sure to configure the switch ports so that they work with the spanning tree protocol and are set as access ports with the correct VLANs required for my users’ wireless connectivity. Moreover, I check if the WAPs are compatible with the protocols and standards that are defined for my switch – such as PoE if they will be powered through the switch. Also, by implementing features such as QoS, I optimize the traffic handed to the wireless interfaces along with the devices connected to the network. This makes communication between the network’s wired and wireless components easier.
Future-proofing your network with scalable switch solutions
When the intricacies of your network become more demanding in the future, there is an urgent need for changes in the design and structure of it. This requires the correct selection of switches that will be able to provide the optimal support for increasing bandwidth requirements or for including more devices as the network expands. It is better to go for the switches that have a modular design so that expanding their capacity is simple, even if it is required to do so without changing the unit entirely. Ensure the switch supports the latest standards, such as 10GbE or higher, and includes features like VLANs and sufficient PoE capacity to meet evolving technological demands. Building strongly on the scalability and modern capabilities of the infrastructure makes it even more easily possible to deploy the network against potential future requirements without compromising on performance.
Ethernet Switch Security: Protecting Your Network
Implementing port security measures
In safeguarding your network from unauthorized access, port security measures are helpful. First set each switch port on a specific number of allowed MAC addresses. Turn on sticky mac address learning in order to automatically associate discovered devices to assigned ports. Set up port users with 802.1X authentication in order to enable only authenticated devices to be connected through the ports. Make sure to keep checking for irregularities in port usage and to disable ports that are not being used, thereby removing excess risk. Adoption of such measures will not only improve the security of the network infrastructure without compromising performance, but it is even more relevant in IoT contexts.
Using VLANs to enhance network security
VLANs are incredibly important for network segmentation and security enhancement. For instance, logically segregating a network into multiple VLANs allows administrators to guard sensitive data and system parts from the general network’s traffic, ensuring that there is less unauthorized access. An example of their application is that HR finance and IT are on different VLANs, which means that these segments do not share devices but have different access to the VLAN.
Current best practices advise users to apply VLAN tagging protocols like IEEE 802.1Q to enhance traffic routing to and from the VLANs in question. To improve security further, placing Access Control Lists between VLANs can be used to reduce the flow of unauthorized data and inhibit lateral movements during compromise attempts. Research results indicate that even a simple but effective measure like segregation of VLANs can decrease the increased exposure of the resources by more than 70 percent. Moreover, pairing VLANs with network analytics tools promotes in-depth traffic monitoring, improving anomaly detection and response efficiency.
In the case of deploying VLANs, it is extremely crucial to keep the audit on configurations up to date and still protect the trunk links between the switches to avoid VLAN hopping attacks. Integrating VLAN isolation with strict security controls and vigilance allows firms to create a robust and maintainable network infrastructure. This approach improves security while improving the networks’ performance and easing the meeting of various industry regulations.
Best practices for switch management and access control
- Implement Role-Based Access Control (RBAC): RBAC helps assign administrative roles on switches to only a selected group. This is implemented to avoid unauthorized modification of switch configurations which would be detrimental for an organization. Organizations which implement RBAC as a policy are able to lower configuration errors by at least 60% which would allow for improved functionality and reliability of the networks.
- Use Secure Protocols for Management Access: Switches are required to be configured to only use management protocols that are deemed secure such as SSH over Telnet. Management networks should also only have access points from certain secure networks. Research shows the probability of interception of wired network within a building and network compromise is lowered to about 25% when employing encrypted management protocols.
- Regularly Update Firmware and Software: To safeguard against any vulnerabilities switch management needs to stay up to date – this also includes the software. Patches and fixes for security loopholes are constantly being released by hardware vendors, and with prompt incorporation of these updates the chances of getting hacked are lowered. Approximately 40% of all cases of switches-related breaches have been caused by a lack of contextual updates to the devices.
- Enable Port Security Features: Avoid utilization of unauthorized devices by implementing port security features on switch interfaces. These include disable policies such as MAC filtering or 802.1X enablement, which restricts accessibility to their sole authorized devices. Port security continues to make networks more secure as insider threats and deployment of rogue devices are lessening in these areas.
- Configure Logging and Monitoring: To enhance visibility across your Ethernet LAN, it is important that you enable logging on switches and combine them with logging and monitoring mechanisms. With the help of real time logging, administrators will be able to monitor suspicious conduct at the earliest. Past research indicates that constant monitoring and alerting can drastically decrease incident response duration by over 50%.
- Disable Unused Ports and Features: To reduce the attack surface, one must reduce network complexity by disabling any unused switch port and features that are auto-negotiation or LLDP (Link Layer Discovery Protocol) t. As a result, this decreases the number of possible access points that an attacker could gain access to.
- Harden Trunk Ports: Enable robust pruning of VLANs so that only the strictly necessary VLANs are allowed through the trunk ports. Implement VLAN pruning and Private VLAN Edge features. Thwarting VLAN hopping attacks can aid in tightening the segmentation of your network by switching the trunk ports. Researchers have demonstrated that effective deployment of VLAN hardening has over 80% reductions in success of such attacks.
- Backup Switch Configurations Regularly: Store switch configurations in a safe location. This guarantees an effective restoration should hardware fail or malicious editing of the settings are performed which is necessary for maintaining a secure ethernet access point. More backups of hardware are automated for easy recovery to reduce downtime.
Altering these best practices will improve the security and reliable and efficient management of the organizations’ switches and access control systems. The result is an agile network that meets the current requirements and is well-secured against future risks.
Frequently Asked Questions (FAQs)

Q: What is the work of ethernet switches?
A: Ethernet switches operate intelligently by connecting devices over the wired network and swapping information packets. Each switch features several ports, and as soon as a packet is received, the switch interrogates the packet’s content to determine the appropriate port for it. While shutting down Mrs. Smith’s computer to eliminate unnecessary traffic, switches allow numerous connections simultaneously. Depending on the switch model, Ethernet switches can handle a variety of transfer speeds starting at 10 Mbps and going as high as 10 Gbps on Layer 2 of the OSI communications model.
Q: What makes a network switch different from an ethernet splitter?
A: A network switch works and is built differently from an ethernet splitter, as the latter performs a completely different function. An array of devices is connected to an ethernet and traffic is always flowing from one device to another, an ethernet switch is wired and controlled, performance is optimized due to simultaneous communication. An ethernet splitter, or passive hub, simply takes one ethernet connection and provides multiple ports that are not managed with traffic, simply echoing one single port input. Most wired networks favor switches since they are much better than passive hubs and provide individual devices to work in their own collision domains.
Q: Can you elaborate on VLAN’s basic principles and its role in conjunction with an ethernet switch?
A: The term “Virtual Local Area Networks” or VLANs refers to the logical subdivision of a network in a way that devices can be grouped together irrespective of their physical location. Such ethernet switches designed to support VLANs enable access to multiple networks which are virtually separated but operate under a single physical network module. This function not only improves security but also boosts network performance and reduces network administrative overhead. VLANs function by specifying an identifier, called a VLAN ID, in the ethernet frame, which allows a switch to send the traffic to all ports that belong to the specified VLAN only, posing as separate broadcasting domains.
Q: Discuss the differences between managed and unmanaged ethernet switches.
A: Managed and unmanaged ethernet switches are differentiated by their configuration capabilities and operating features. Unmanaged switches, such as the Netgear 8-port Gigabit Ethernet Unmanaged plug-and-play switch, are configuration-free devices as they can start functioning once plugged into a network. These devices are suited for home and low office-type networking needs. On the contrary, managed switches function more sophisticatedly than the basic network hardware; they have functions such as support for VLANs, QoS (Quality of service), port mirroring capabilities, and remote access and management. Large networks and those networks that require advanced control security features are ideal for such types of managed switches. While such managed devices are costlier than unmanaged switches, they do have a greater degree of flexibility and allow for scaling of growing networks.
Q: What Exactly Is PoE Technology And What Are Its Semiconductor Telecommunications Switches?
A: Power over Ethernet (PoE) Works, Meaning that it links the data to the communication device via ethernet cables; Ethernet allows devices to receive both data and electricity. This then renders VoIP phones, IP cameras, and wireless access points, amongst others, usable with power over ethernet switches as their handsets need not be paired with additional power cables. The IEEE 802.3af or IEEE 802.3at standards are usually applicable to these switches. The 4 Port PoE switches, for example, have more than 1 ethernet port, allowing a user to switch from PoE-enabled devices to a standard ethernet mode to introduce more versatility into the connectivity landscape. This eliminates redundancy, lowers installation expenditures, and paves room for more efficient device placement across networks.
Q: What key details do I need to determine signing off on an ethernet network switch to be placed in my home or office?
A: Some of the key details to consider are as follows when selecting an ethernet network switch for your home or office: 1. Number of ports: Select a switch that offers multiple ports that cover your needs and also the future needs (e.g., 5-port, 8-port or more). 2. Speed: How many ports do you require a Gigabit switch (1000 Mbps), or would a Fast Ethernet switch (100 Mbps) be enough? 3. Form factor: A desktop or wall mount switch based on the space that is available at your disposal. 4. Managed vs Unmanaged: Do you require advanced features such as VLANs, or would a plug-and-play solution be good enough. 5. PoE support: If your devices can use Power over Ethernet, seek out the switches with PoE capabilities. 6. Brand reputation: Seek out trusted brands such as Netgear for additional reliability and support. 7. Scalability: Make sure that the switch can support the potential growth of the network.
Q: What benefits do I get from using an ethernet network switch on my home or office ethernet setup?
A: An ethernet network switch can significantly improve your home or office ethernet in various ways: 1. Connectivity: It enables more ethernet ports, which means more wired devices can be hooked onto the network. 2. Better performance: Switches allow the creation of multiple collision domains on a network, thus reducing congestion on every port, further increasing the response time. 3. Greater reliability: For stationary devices in an Ethernet LAN setup, connections through a switch tend to be more reliable than wireless. 4. Fast-paced applications support: For instance, gigabit switches can transfer data much more smoothly, which is essential for sharing large files and streaming videos. 5. Easy Expansion: Your network will expand whenever there are new requirements. 6. PoE functionality: Most switches can power devices like IP cameras or VoIP phones. 7. VLAN: Managing switches are equipped with unique features such as VLANs, meaning traffic can be separated from each other using security-enhancing features.
Reference Sources
1. Transition to SDN is HARMLESS: Hybrid Architecture for Migrating Legacy Ethernet Switches to SDN
- Authors: Csikor, Levente et al.
- Published in: IEEE/ACM Transactions on Networking, 2020
- Summary: This research claims to put forward a new design of SDN switch called as HARMLESS which enables the old Ethernet switches to incorporate SDN features without a hassle through a straightforward approach. This is done by reverse engineering the software for an OpenFlow switch in another software module, which allows for a cheap and efficient combination of SDN in the existing infrastructure without losing any competitive edge.
- Key Findings: HARMLESS is capable of achieving SDN deployment cost reductions for new small businesses and meeting or even surpassing the existing data plane performance metrics as competitive solutions generally do, especially for smaller companies,
- Methodology: The authors engaged in performance tests of HARMLESS against traditional SDN solutions with the help of Csikor, Levente et. Al 2020, ranging from throughput to latency(Csikor et al., 2020, pp. 275–288).
2. Deterministic TCP Incast Suppression Technique as Utilized to COTS Switch Ethernet-Servers Network Systems by Altering IP Packet Sizing Parameters
- Authors: Jiawei Huang et al
- Published in: IEEE Cloud Computing Journal, 2020.
- Summary: The problem of TCP Incast in data center networks that may otherwise lead to throughput collapse because of packet loss that occurs on shallow-buffered Ethernet switches is discussed by the authors. The authors suggest a solution to this, referred to as Packet Slicing, that simply modifies the size of the IP packets.
- Key Findings: The method, when implemented, has been shown to nearly allow for the goodput of various data center TCP protocols to be 26 times higher on average, with the Effect on switches and end hosts’ I/O performance being minimal.
- Methodology: It was established that Packet Slicing is an effective tool through theoretical analysis, as well as, the usage of empirical testing on a physical testbed (Huang et al., 2020, pp 749-763).
3. Redesigning Buffer Handling in Lossless Ethernet
- Authors: Hanlin Huang And Other Authors
- Published in: IEEE/ACM Transactions on Networking, 2024
- Summary: Selective PFC is a buffer management technique that aims to resolve the interpretive flow control difficulties prevalent in lossless Ethernet networks that ensue due to applying end-to-end-biased congestion control utilization and hop-by-hop flow control complementarily. The approach centralizes on the advancement of buffer space assignment dynamically adjusted to fit traffic conditions on the network.
- Key Findings: The implementation of Selective-PFC translates to approximately 69% reduction in the number of percentage frames, and are also associated with a reduction in terms of average flow completion time preferences for extremely large victim flows.
- Methodology: This paper has filled the gap because such studies did not analyze the integration of such processes with the sonosuk buffer management (Huang et al., 2024, pp. 4749–4764) composite approach.
