Table of Contents
ToggleHierarchical Network Design
Concept
Hierarchical network design is a network architecture approach to build reliable, scalable, and efficient computer network systems. The design methodology achieves better management, performance, and security by dividing the network into different layers, each with specific functions and responsibilities. Originally introduced by Cisco in 2002, hierarchical network design has become a standard practice in many network designs.
In traditional flat network designs, networks are connected using hubs and switches, which become difficult to manage and maintain as they scale. The introduction of hierarchical network design addresses these challenges by dividing the network into different layers to better control traffic, improve response times, and optimize network performance.
Hierarchy
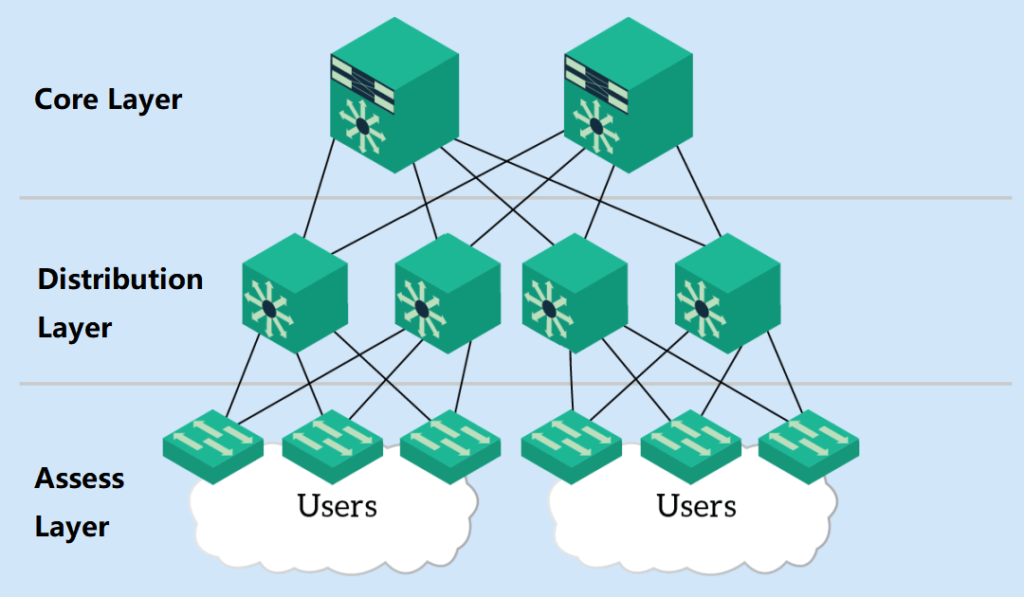
A hierarchical network design usually consists of the following major layers:
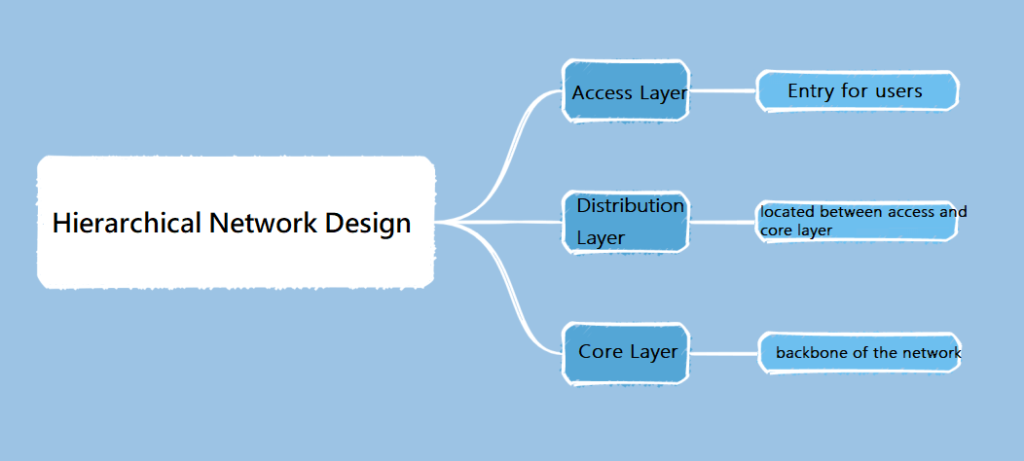
1. Access Layer: This is the entry point for user devices (e.g., computers, cell phones, printers, etc.) to access the network. The access layer is responsible for providing user access, authentication, security policies, and other functions, but also performs local traffic processing. Switches play a key role in this layer, connecting user devices to the network.
2. Distribution Layer: The distribution layer is located between the access layer and the core layer, and is responsible for connecting different access layer subnets. At the distribution layer, traffic is aggregated and filtered, as well as segregated between sectors (through virtual LAN or VLAN technology).
3. Core Layer: The core layer is the backbone of the network and is responsible for high-speed data transmission and traffic exchange. It connects the different aggregation layers and provides high network availability and redundancy. The core layer needs to be characterized by high bandwidth, low latency, and high availability.
Advantages
Advantages of hierarchical network design include:
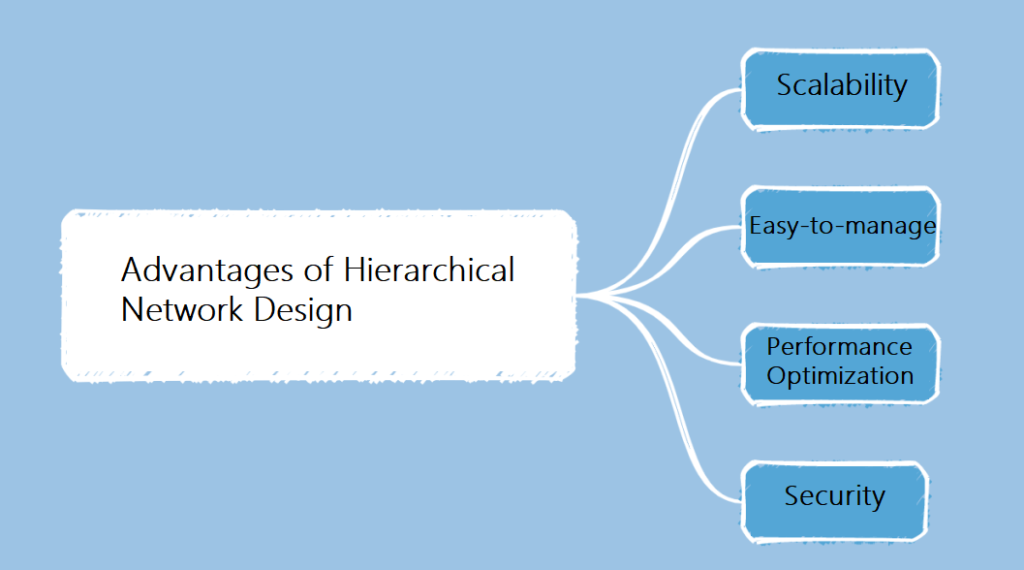
- Scalability: The hierarchical design makes it easier to scale the network horizontally, as users and devices increase.
- Easy to manage: Each layer has clearly defined functions and responsibilities, making network management easier and more controllable.
- Performance Optimization: The hierarchical design allows for traffic control and optimization at different levels to provide better network performance and response times.
- Security: The hierarchical design supports the implementation of security policies and allows access control at the access and aggregation layers to improve network security.
Core Layer
The core layer is the backbone of the network, which is responsible for transmitting data between the various parts of the network at high speed and high efficiency. The core layer usually consists of a number of high-speed, high-capacity devices, such as routers and switches. At this layer, the main task is to transfer data from one point to another as quickly as possible without complex processing or decision-making. Therefore, the design and management of the core layer needs to focus on the performance and bandwidth of the devices, as well as the reliability and redundancy of the network.
Features
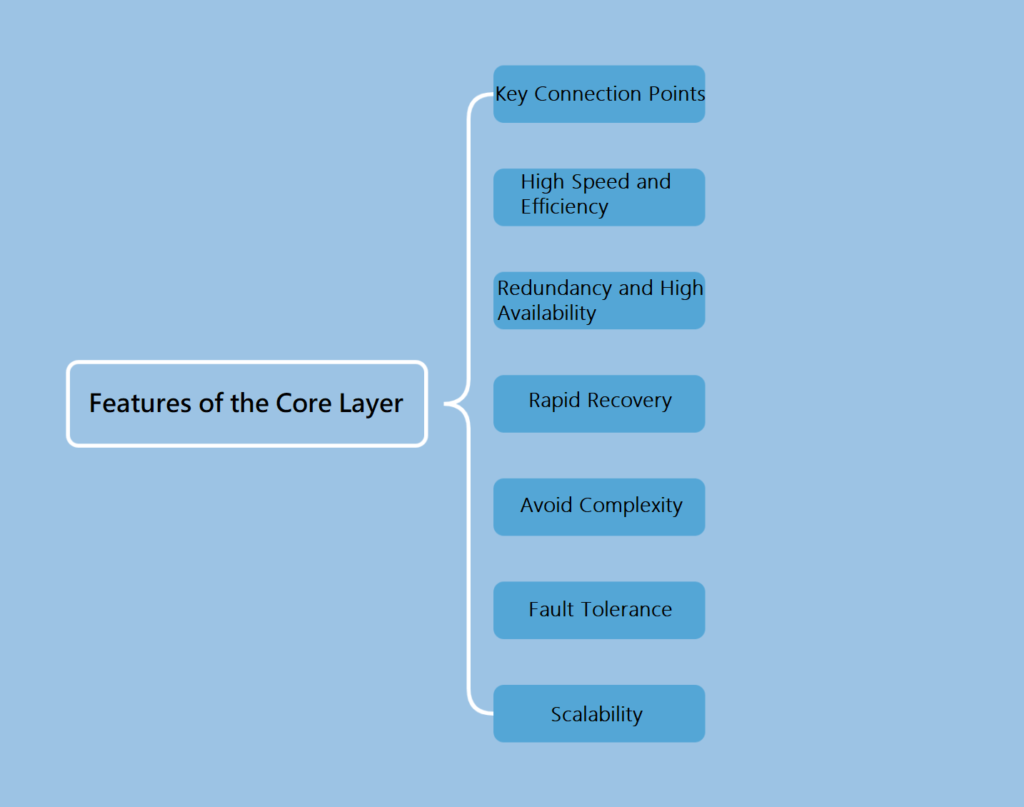
Key Connection Points: The core layer connects different network components such as the aggregation layer and the access layer. It is the main conduit for the flow of data through the network and therefore needs to be characterized by high bandwidth and low latency to ensure that data can be transmitted quickly and efficiently.
High Speed and Efficiency: The main task of the core layer is to pass large amounts of data quickly. Therefore, the core layer should use high-speed switching equipment to support high-speed data transmission in the network.
Redundancy and High Availability: Due to the importance of the core layer, the network design should consider redundancy to avoid a single point of failure. Use technologies such as redundant links and hot backup devices to ensure that the network remains available in the event of a failure.
Rapid Recovery: In the event of a core layer failure, the network needs to be able to recover quickly. Fast fault detection and switching mechanisms can reduce the impact of network disruption and ensure business continuity.
Avoid Complexity: The core layer should be kept as simple as possible, avoiding complex packet operations. This helps to increase the efficiency of data transmission and reduces potential points of failure.
Fault Tolerance: The core layer equipment should have good fault tolerance and be able to handle high loads and abnormal conditions to ensure network stability.
Scalability: Although the number of devices in the core layer is relatively small, they should still be scalable. By using high-quality equipment, the core layer can be expanded without sacrificing performance.
Typical Devices
High-Performance Switch: The core layer requires high bandwidth and low latency to support large amounts of data transmission in the network. High-performance switches usually have high throughput and fast forwarding capabilities to meet the needs of the core layer.
Routers: In some networks, the core layer may include routers to handle routing and packet forwarding between different subnets. These routers need to have high-speed routing and forwarding capabilities to ensure fast data transmission.
Layer 3 Switch: Layer 3 switches can play a dual role in switching and routing functions in the core layer. They can support high-speed data forwarding and complex network policies.
High Availability Switch: In order to ensure the reliability of the core layer, high availability switches are usually equipped with redundant links, hot backups, and fast fail-over capabilities. These features ensure rapid recovery in the event of a failure.
Modular Switch: Modular switches allow different types of modules to be added as needed to meet different network requirements. These switches often have the flexibility to configure ports and features.
Data Center Switch: In large-scale data center networks, the core layer may include data center switches specifically designed to support large-scale data transfers, virtualization, and cloud computing.
Distribution Layer
The distribution layer (also known as the aggregation or convergence layer) is located in the middle level of the network and is responsible for processing and distributing data from the access layer to the core layer. Devices at the aggregation layer typically need to have higher processing power because they are required to make more complex decisions, such as routing based on network policies. In addition, the convergence layer is where security policies and quality of service (QoS) controls are enforced.
Characteristics
Traffic Aggregation and Distribution: The primary responsibility of the convergence layer is to aggregate incoming traffic from the access layer and distribute it to the rest of the network. This helps avoid overloading the core layer while optimizing the performance of the entire network.
Multiple Switches and Routers: The aggregation layer typically consists of multiple switches and routers (or Layer 3 switches), each of which connects to multiple devices in the access layer. The connections between these devices allow traffic to flow between different subnets.
Boundaries and Distribution Blocks: The distribution layer itself acts as the boundary of the network, creating a relatively separate block of the network. These distribution blocks allow traffic to be routed from one block to another through the core layer. The advantage of distribution blocks is that problems in one block do not spill over to the rest of the network, thus increasing the availability and maintainability of the network.
Applying Network Policies: The aggregation layer is where network policies are applied and where access control, traffic restriction, and other security policies can be enforced. This helps protect the network from unauthorized access and malicious behavior.
Additional Security Layer: The distribution layer not only connects the access layer to the core layer but also acts as an additional security layer between the access layer and the entire network. By implementing access control and other security measures, the aggregation layer enhances the overall security of the network.
Segregation and Isolation: The aggregation layer allows for segregation between different departments, functions, or user groups through methods such as VLAN technology. This helps to minimize potential interference and conflicts and improves the manageability of the network.
Typical Devices
Layer 3 Switches: Layer 3 switches are equipped with switching and routing capabilities that enable fast traffic delivery and routing in a network. They are often capable of handling more complex network policies such as VLAN segregation, inter-subnet routing, and so on.
Distribution Router: In some network architectures, the aggregation layer may include distribution routers to handle traffic aggregation and routing. These routers are capable of connecting multiple access layer subnets and directing traffic to the core layer or other destinations.
Aggregation Switches: Aggregation switches are specifically designed to connect multiple access layer switches or devices, aggregating and directing their traffic to the core layer. These switches typically have high-speed switching capabilities and a large number of ports.
Routing Switches: Routing switches integrate switching and routing functions, allowing fast forwarding and routing decisions between the network and link layers. They can handle complex network topologies and routing tables.
Multilayer Switch: Multilayer switches combine switching and routing functions and are typically used to handle aggregation layer tasks, supporting VLAN segmentation, routing, and load balancing.
Access Layer
The access layer (also known as the edge layer) is the outermost layer of the network and is responsible for connecting end-user devices such as computers, cell phones, and other network devices. At the access layer, devices typically need to handle a large number of low-speed, low-volume connections and provide various services such as Dynamic Host Configuration Protocol (DHCP) and Network Address Translation (NAT). The design and management of the access layer needs to take into account the user’s needs and experience, as well as the number and type of devices.
Characteristics
User Device Connection Point: The access layer is the entry point for user devices (e.g., laptops, smartphones, tablets, printers, etc.) to connect to the network. The end user realizes access to network resources through the access layer.
Switch Density: Because of the large number of user devices connected, the access layer usually requires the deployment of high-density switches. These switches need to have a high port density to support the connection of multiple user devices.
Abundance of Functions: Access layer switches need to be equipped with a rich set of functions to meet the needs of different user devices. These features may include discovery and configuration, security authentication, QoS marking, routing protocols, spanning tree protocols, and more.
Security: The access layer is the first boundary of the network and needs to be highly secure. By using technologies such as 802.1X authentication, port security, and VLAN isolation, unauthorized devices can be prevented from accessing the network.
Network Identification: Through DHCP, 802.1X authentication, and other mechanisms, the access layer can identify and control the devices connected to the network to ensure that only legitimate devices can access the network.
QoS Support: The access layer needs to support QoS (Quality of Service) to ensure that network resources are allocated appropriately. Labeling, policing, and queuing traffic ensures that critical applications receive adequate bandwidth.
Physical Infrastructure Support: Access layer switches typically support PoE (Power over Ethernet), which provides power to some devices (e.g., IP phones, cameras) and simplifies cabling requirements.
Connection to the Aggregation Layer: The feed from the access layer into the aggregation layer means that user devices establish a connection at the switch in the access layer. The aggregation layer further flows the data to the core layer, enabling the flow of data between different network layers.
Typical Equipment
Access Switch: Access switches are key devices for connecting user devices. They usually have a high port density and support the connection of multiple user devices. Access layer switches provide basic network connectivity and switching functions.
Wireless Access Points (WAPs): In a wireless network environment, WAPs are key devices that connect wireless devices (e.g., laptops, smartphones) to the network. They provide Wi-Fi connectivity and enable mobile devices to access network resources.
Network Switches: In addition to access layer switches, regular network switches may be used in some scenarios. They can be connected to the access layer switch to realize the connection of multiple user devices.
802.1X Authentication Server: The access layer needs to implement security authentication to ensure that only authorized devices can access the network. 802.1X authentication servers are used to verify the identity of user devices and implement access control.
VLAN Management Devices: The access layer may need to implement VLAN (Virtual LAN) segregation to isolate different user devices in different virtual networks; VLAN management devices are used to configure and manage different VLANs.
Power over Ethernet Switch: To simplify powering devices, the access layer may use PoE switches, which are capable of powering a number of devices (e.g., IP phones, cameras).
Network Access Control Server: A NAC server is used to enforce network access control and ensure that devices connected to the network meet security policies and compliance requirements.
Comparison
| Aspect | Core Layer | Distribution Layer | Access Layer |
| Functions | – High-speed data transfer to support high throughput – Redundancy and high availability – Fast recovery and load balancing | – Traffic aggregation and distribution, connecting different subnets – Apply network policies, QoS marking – Horizontal scaling and redundancy | – Connecting end-user devices – Support for a large number of connected devices, high port density – Secure authentication, network identity, QoS support |
| Hardware Requirements | – High-bandwidth, low-latency switching equipment – Redundant links and hot standby – High reliability and fault tolerance | – High-speed switching equipment with support for traffic aggregation – Multiple switches and routers – Hot standby and redundant links | – High-density switch to support a large number of user connections – PoE support for power provisioning – Security features and QoS support |
| Security | – Boundary security to restrict external access – Protects the core network from unauthorized access | – Apply network policy, access control – Segregate different departments, user groups – Prevent unauthorized access | – First border, a high level of security required – 802.1X authentication, port security – Prevent unauthorized device access |
| Scalability | – Quality (better device) scaling – Avoids CPU-intensive operations | – Supports quality rather than quantity scaling – Highly Scalable | – Supports a large number of device connections, highly scalable – Simplifies device addition and management – Expanding the number of devices |
| Management and Maintenance | – Simplified design with fewer points of failure – Redundant design to reduce single points of failure – High availability and fast recovery | – Distributed block management, problems do not affect other parts – High availability and maintainability | – Device diversity and management complexity – Need to maintain a large number of connected devices – Challenges of device management, troubleshooting, and security policy enforcement |
Conclusion
Network hierarchy mapping is a complex but important task. It requires the network engineer to be thoughtful about the needs and resources of the network and to design an efficient, reliable, and manageable architecture for the entire network. Understanding the functions and requirements of the core, distribution, and access layers is critical to accomplishing this task.
Related Products:
-
 QSFP28-100G-SR4 100G QSFP28 SR4 850nm 100m MTP/MPO MMF DDM Transceiver Module
$40.00
QSFP28-100G-SR4 100G QSFP28 SR4 850nm 100m MTP/MPO MMF DDM Transceiver Module
$40.00
-
 QSFP28-100G-IR4 100G QSFP28 IR4 1310nm (CWDM4) 2km LC SMF DDM Transceiver Module
$110.00
QSFP28-100G-IR4 100G QSFP28 IR4 1310nm (CWDM4) 2km LC SMF DDM Transceiver Module
$110.00
-
 QSFP28-100G-FR1 100G QSFP28 Single Lambda FR 1310nm 2km LC SMF with FEC DDM Optical Transceiver
$215.00
QSFP28-100G-FR1 100G QSFP28 Single Lambda FR 1310nm 2km LC SMF with FEC DDM Optical Transceiver
$215.00
-
 QSFP28-100G-DR1 100G QSFP28 Single Lambda DR 1310nm 500m LC SMF with FEC DDM Optical Transceiver
$180.00
QSFP28-100G-DR1 100G QSFP28 Single Lambda DR 1310nm 500m LC SMF with FEC DDM Optical Transceiver
$180.00
-
 Q28-100G23-BX10 100G QSFP28 BIDI TX1271nm/RX1331nm PAM4 Single Lambda LC SMF 10km DDM Optical Transceiver Module
$500.00
Q28-100G23-BX10 100G QSFP28 BIDI TX1271nm/RX1331nm PAM4 Single Lambda LC SMF 10km DDM Optical Transceiver Module
$500.00
-
 QSFP-DD-400G-SR8 400G QSFP-DD SR8 PAM4 850nm 100m MTP/MPO OM3 FEC Optical Transceiver Module
$149.00
QSFP-DD-400G-SR8 400G QSFP-DD SR8 PAM4 850nm 100m MTP/MPO OM3 FEC Optical Transceiver Module
$149.00
-
 QSFP-DD-400G-DR4 400G QSFP-DD DR4 PAM4 1310nm 500m MTP/MPO SMF FEC Optical Transceiver Module
$400.00
QSFP-DD-400G-DR4 400G QSFP-DD DR4 PAM4 1310nm 500m MTP/MPO SMF FEC Optical Transceiver Module
$400.00
-
 QSFP-DD-400G-LR4 400G QSFP-DD LR4 PAM4 CWDM4 10km LC SMF FEC Optical Transceiver Module
$600.00
QSFP-DD-400G-LR4 400G QSFP-DD LR4 PAM4 CWDM4 10km LC SMF FEC Optical Transceiver Module
$600.00
-
 QSFP-DD-400G-FR4 400G QSFP-DD FR4 PAM4 CWDM4 2km LC SMF FEC Optical Transceiver Module
$500.00
QSFP-DD-400G-FR4 400G QSFP-DD FR4 PAM4 CWDM4 2km LC SMF FEC Optical Transceiver Module
$500.00
-
 QSFP-DD-400G-ER4 400G QSFP-DD ER4 PAM4 LWDM4 40km LC SMF without FEC Optical Transceiver Module
$3500.00
QSFP-DD-400G-ER4 400G QSFP-DD ER4 PAM4 LWDM4 40km LC SMF without FEC Optical Transceiver Module
$3500.00
-
 QSFP-DD-800G-FR4 800G QSFP-DD800 FR4 (200G per line) PAM4 CWDM 2km DOM Duplex LC SMF Optical Transceiver Module
$3500.00
QSFP-DD-800G-FR4 800G QSFP-DD800 FR4 (200G per line) PAM4 CWDM 2km DOM Duplex LC SMF Optical Transceiver Module
$3500.00
-
 QSFP-DD-800G-DR4 800G QSFP-DD800 DR4 (200G per line) 1311nm 500m Dual MPO-12 SMF Transceivers
$2850.00
QSFP-DD-800G-DR4 800G QSFP-DD800 DR4 (200G per line) 1311nm 500m Dual MPO-12 SMF Transceivers
$2850.00
-
 OSFP-800G-SR8D-FLT OSFP 8x100G SR8 Flat Top PAM4 850nm 100m DOM Dual MPO-12 MMF Optical Transceiver Module
$650.00
OSFP-800G-SR8D-FLT OSFP 8x100G SR8 Flat Top PAM4 850nm 100m DOM Dual MPO-12 MMF Optical Transceiver Module
$650.00
-
 QSFP-DD-800G-DR8D QSFP-DD 8x100G DR PAM4 1310nm 500m DOM Dual MPO-12 SMF Optical Transceiver Module
$1250.00
QSFP-DD-800G-DR8D QSFP-DD 8x100G DR PAM4 1310nm 500m DOM Dual MPO-12 SMF Optical Transceiver Module
$1250.00
-
 QSFP-DD-800G-FR8 QSFP-DD 8x100G FR PAM4 1310nm 2km DOM MPO-16 SMF Optical Transceiver Module
$1500.00
QSFP-DD-800G-FR8 QSFP-DD 8x100G FR PAM4 1310nm 2km DOM MPO-16 SMF Optical Transceiver Module
$1500.00
-
 QSFP-DD-800G-LR8 QSFP-DD 8x100G LR PAM4 1310nm 10km MPO-16 SMF FEC Optical Transceiver Module
$1600.00
QSFP-DD-800G-LR8 QSFP-DD 8x100G LR PAM4 1310nm 10km MPO-16 SMF FEC Optical Transceiver Module
$1600.00
















