Every organization has to put a premium on the reliability and efficiency of its network infrastructure and associated physical resources. Access switches are at the core of this infrastructure, representing the first interaction of end-user equipment with corporate networking features. This blog will thoroughly examine access switches and present their essential functions in terms of operating with data traffic in the networks, ensuring security, and growing potential for expansion. Further, in this document, such readers will better understand how the devices can be arranged within a network to allow fast interactions, making proper use of the potential available in such devices. As we specifically cover the technical features of the access switches and their strategic applications, the readers will appreciate how to configure an efficient network structure that can adequately address the requirements of a particular enterprise.
Table of Contents
ToggleWhat is an Access Switch and How Does it Work?
Definition and Functions of an Access Switch
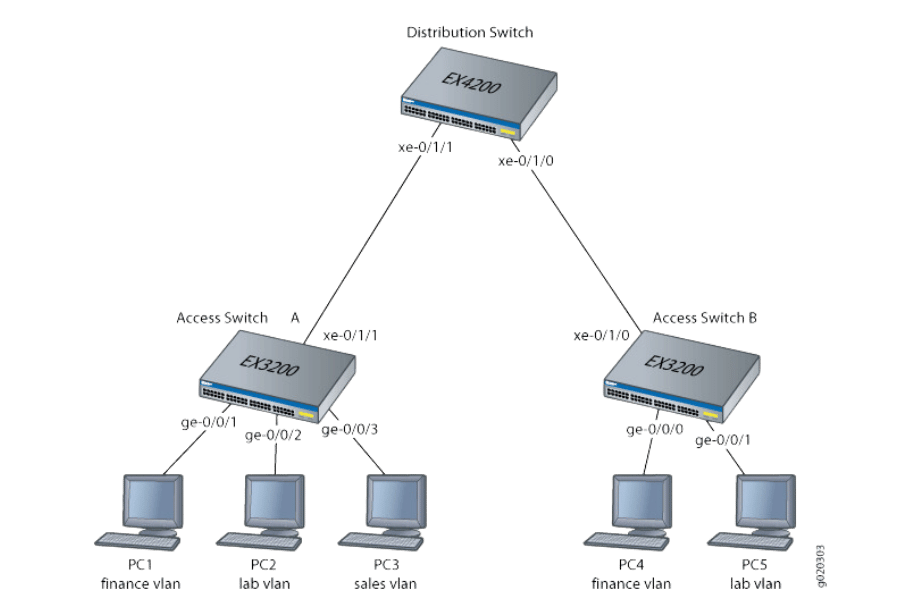
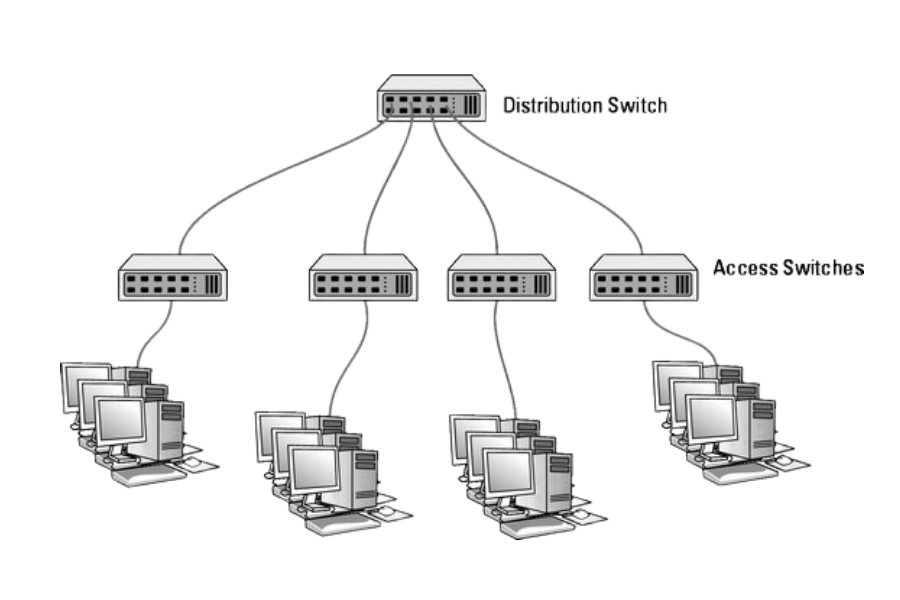
An access switch or layer two switch is a device used to connect the end-user equipment, including computers, printers, and IP telephones, to the wider organization’s network. It assists mainly in the switching of incoming and outgoing data packets to the right destination, as specified in MAC address tables. Access switches are essential in isolating communication faults on a network’s traffic giving way to better speed and security by the use of VLANs and activating port security features. These switches form part of the numerous ports which serve most of the ports of the network—making it crucial in providing optimal network connections from the core to the periphery of an organizational network design architecture.
What Role Do Access Switches Play within a Network?
Within a network, access switches are the elements that connect the devices to the core network. These are network components deployed on the periphery of a network where end-user devices connect to distribution switches or routers. Access switches can also act to manage and control data flows on the network by incorporating features such as VLAN, which helps organize different types of network traffic within the same switching device. Furthermore, other devices, such as switches, can be combined with 802.1X. This is essential for network security design since it permits access limited to authenticated end terminals and control access to the network. This integration allows proper data exchange and contributes to the overall efficiency and growth of the network.
The Difference Between an Access Switch and a Core Switch
Although access switches and core switches perform their unique functions within the network hierarchy, they fall under two broad categories of switches. Access switches are located at the network’s periphery, linking end devices to the network and managing local traffic. They perform roles like traffic isolation and enforcing security policies. Core switches, on the other hand, are situated at the network core or backbone. They are built to handle masses of traffic at high speed and efficiency, as well as support core functions and interconnecting distribution switches. Access switches focus on granting user access and applying security measures, while core switches work on the parameters of speed and reliability encompassing the whole network.
How to Choose Access Switch For Your Network?
Considerations in Features of Access Switches
There are additional factors besides the cost that one should consider when choosing an access switch for their network to facilitate optimum performance and scalability. First of all, it is necessary to evaluate how many ports one needs, including the port density, to prepare for the design’s current and future expansion. Another important feature of the switch should be the ability to provide PoE since the powering of IP phones and wireless access points are often required. Furthermore, the evaluation should include at least Layers 2 and 3, which can provide enhanced routing and switching features. Some of the additional functionalities, such as access control lists (ACLs) and 802.1X authentication mechanisms, are vital; therefore, security should also be a factor. Finally, for effective network management, it is important for the switch to support VLANs and popular network management protocols such as SNMP for configuration management.
Examining Port Density and PoE
Port density is the metric that defines the switch’s number of ports and, thus, how many devices can be hooked to it. High port density features are more useful for growth potential and future network extension with no extra hardware required. It facilitates optimal utilization of expanding space and resources in any network design. Power Over Ethernet allows electric power to be sent in the process of sending data through the Ethernet cabling, making it possible to do away with a power supply as each device gets its power supply from an Ethernet connection. This is very important to devices like IP cameras, wireless access points, and VoIP phones since the power supply provision is streamlined, and cabling is better managed. When selecting an access switch in addition to its adequacy in terms of port density and those supporting PoE, ensure that networking infrastructure is as flexible and sound as possible.
Use of Fiber Optics in Access Layer Switches
Fiber optic technology is critical in the access layer switches as it allows fast and far-reaching communications with little signal loss. This becomes especially important when connecting switches across long distances, as is often the case in large campuses or data centers since it has much more bandwidth than copper cables. Fiber optic cables improve network effectiveness and coherence by decreasing electromagnetic noise. The same attachments help combine high-tech services that require transferring a lot of information. The use of fiber optic in the access layer switches is beneficial for the upgradability of the networks to higher data rates while providing dependable and scalable connectivity solutions.”
Why Use a Cisco Catalyst for Your Access Layer?

Benefits of Cisco Access Switches
Cisco access switches offer a rugged, dependable, and highly customizable set of devices that cater to varying network needs. Other important merits include enhanced security through features like TrustSec, which offers controlled access and network segmentation. Cisco core switches are easy to scale up with minimal interferences to the network operations since further enhancements are made in expansion. They further increase operational efficiency concerning the mounting of high port densities and multi-gigabit and gigabit lawyers whose application is necessary because of the increasing need for handling the huge volume of data traffic over the networks. In addition, Cisco also provides its users with simpler network management platforms such as DNA Center. Such technological advances help lessen operational burdens and maximize the productivity of the IT workforce since less time is spent on routine tasks. Cisco makes sure that the access switches are periodically updated with new software and receive continuous support to keep up with the current trends of connectivity and use cases.
Differentiating Cisco Catalyst from the other brands
A few key points can be mentioned when analyzing Cisco Catalyst Switch and any other brand in the same category. Security is one of the celebrated aspects of Cisco Catalyst switches, especially in access control features, most notably TrustSec. Regarding management capacity, Cisco specializes in providing non-invasive enhancement and growth, which other companies may not always offer. Regarding functionality, Catalyst switches come in high port dens – gigabit or even multigigabit ethernet Ethernet ports that cater to heavy data traffic. Furthermore, Cisco’s integrated management, DNA Center, provides some superior automation and monitoring functions, performing operations that are deeper than many brands offer. Last but not least, the consistent progression of software and adequate support that Cisco provides make sure that their switches will always comply with and be safe in a fast-paced, changing environment.
Deployment Strategies for Cisco Access Layer Switches
It is worth stating that Cisco Access Layer Switches should be deployed using a strategy that improves the network’s efficiency, security, and future expandability. Firstly, the deployment should be prepared. This is performed by determining the requirements of the network now and shortly. This involves placing switches in such a way as to provide coverage and connectivity. Secondly, Taking advantage of Cisco’s cutting-edge automation equipment, such as DNA Center, makes this process for configuration and management more efficient with less human effort and, therefore, chances of error. Strong security mechanisms, including TrustSec, are important in safeguarding the level of security required and protecting the resources throughout the network. Lastly, don’t forget about the constant monitoring and maintenance of the hardware with the help of Cisco’s software updates, which will help keep the system intact and relevant to new advancements and threats. By observing these strategies, companies can reap the benefits of effective and efficient Cisco Access Layer Switches.
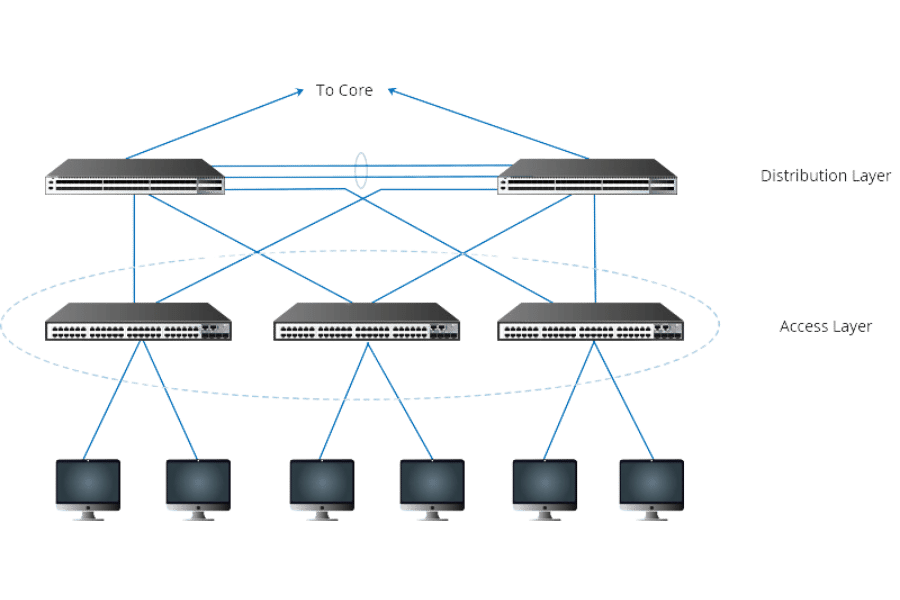
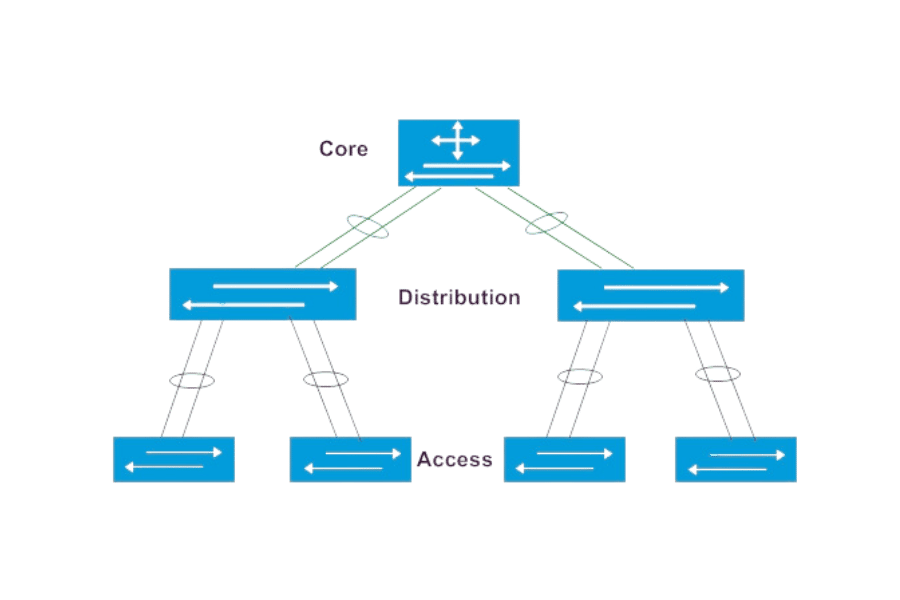
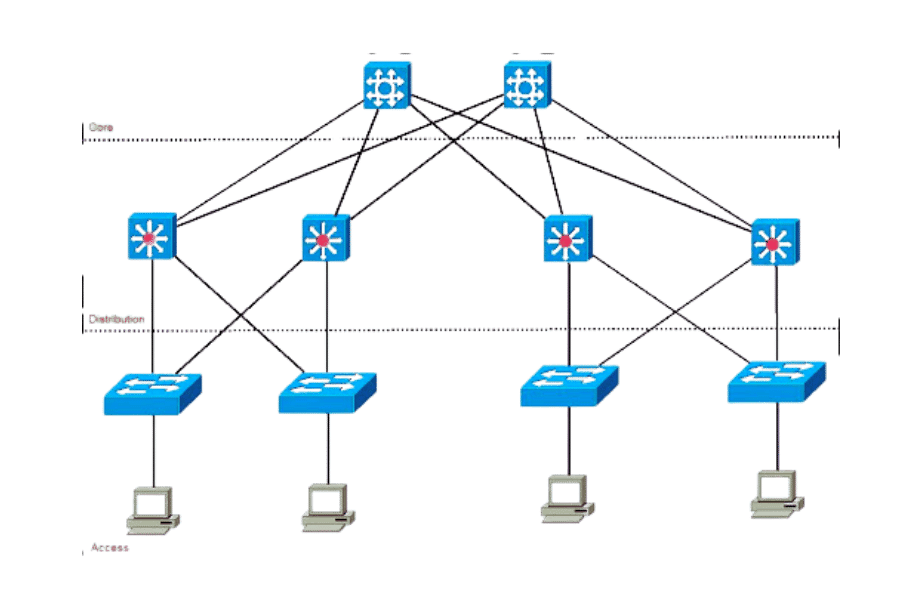
How Do Access Switches Fit Into the Hierarchical Network Model?
The Access Layer in the Network
The bottom level of a hierarchical model is called the Access Layer because it is the layering where all endpoints, such as computers, printers, and other resources, connect to the network. This layer performs basic network connectivity functions and plays an important role in interfacing end devices with the upper tiers of the network structure by managing the distribution of information. Access switches, such as Cisco access layer switches, play this role by providing stable and secure interfaces and efficient connections that offer sufficient bandwidth and network resources for client devices. On the other hand, by managing the ingress traffic efficiently, the Access Layer considerably improves, enhances, and secures the entire network system.
Role of Access Points in a LAN
Access Points (APs) are the key points in a Local Area Network (LAN) where wireless devices connect with the communication network. APs serve as machines linked to the wired network and provide mobile devices with broadband wire-less connection, enabling the combination of wireless and wired devices in one network. They are employed in handling wireless traffic communication rates in networks where they transmit, receive, and retransmit data from client devices to the network and vice versa. Furthermore, access points allow the implementation of many other security mechanisms as well as the limited assignment of bandwidth, making LANs more productive, scalable, and secure.
Integration of Core and Distribution Switches
I intend to maintain a sound network complemented by access points and switches on the core and distribution layers through information sourced from backbone industries. The access switches connect to the distribution switches to sum the traffic, which goes further to the core where all the load balancing, high-speed routing, and redundancy are done. Key factors in this process are the available capacities on the switch uplinks, usually requiring a 10 Gbps interface or more for adequate throughput. Redundancy is also improved by allowing multiple paths through link aggregation protocols such as LACP. There is no doubt that the practice of some advanced users in de-cluttering the traffic flow using VLAN segmentation techniques makes the network secure and the bed of efficient data processes: such information has been propped by experts independent of time. It can be seen that all these ways help each layer actively state its requirements and, on the other hand, assist layers in the performance under the conditions of network demands, as helped by the advanced resources on Google.com.
What is the current market growth of Ethernet Access Switches?
Improvements in Gigabit Ethernet Technologies
The latest progression of the megabits Ethernet technologies can be illustrated in noteworthy speed, up-scaling, and efficient usage. The emergence of multigigabit Ethernet, for example, 2.5G and 5G Ethernet, allows data transfers through the existing cable networks, enhancing upgrades without extensive rewiring. Power, included in the Power over Ethernet (PoE) developments, extends the markets of high-wattage devices in smart building technology and Internet of Things applications. Another development area is even energy-efficient Ethernet, which reduces the power consumed by the device based on the network activity. These innovations allow networks to effectively handle higher traffic, supporting new technologies while keeping operational costs reasonable.
Impact of 10GbE Switches on Access Layer
The introduction of 10 Gigabit Ethernet (10GbE) switches at the access layer has been proven to boost network performance and capacity greatly. First and foremost, the additional bandwidth offered improves the data throughput, which is quite vital for modern applications that require high speeds for data access and/or data transfer. Thus, this shift guarantees that network latency is kept to a minimum, increasing application responsiveness. In addition, connectivity using 10GbE switches helps to manage high-concentration areas much better due to the increased number of connected devices without any sacrifice on speed or reliability. Further, these switches provide provisions for advanced QoS (Quality of Service), enabling management of traffic needed for efficient use of the network resources. Thus, the scope of deployment of the 10GbE switches is very much pertinent in the quest of making the tensile network infrastructure progress with time.
Enhancing Security of Networks Through the Use of Port Security Ultima
As part of network security maintenance, port security is key in controlling switch port usage by taking into account MAC addresses so that ties with other devices can be minimized. In regard to the port access control to devices MAC address as well as the configuration, this feature is useful in ameliorating the chances of MAC spoofing and unwanted access as it caps the quantity of devices permitted on a single port per MAC address. This is a two-staged approach where the development team takes care of first the physical configuration of each switch port and carried out the practical aspect of using soft or woody magic trees. One of them is port security and when measures to secure the network are unnecessary then power is cut to the port or an alarm goes off or in fact other measures are taken to prevent any unauthorised use of network resources. Such strategies are very useful in protecting as well as safeguarding the network information from being compromised by any unauthorized individual.
Reference Sources
Frequently Asked Questions (FAQs)
Q: What is an access switch, and what is its purpose in a network?
A: An access switch can be defined as the first point of connection that the devices or end users have to make the network available. It takes information from the end users, which includes computers, telephone sets, printers, etc., and sends it forth to the distribution and core layers. These devices are intended for end users’ connectivity and are usually located on the frontier of the networks.
Q: What makes access switches different from distribution and core layer switches?
A: Access layer switches link up the end devices, while distribution and core layer switches work differently. The distribution layer collects traffic from several access layer switches and enables connectivity per the preset policies. The function of core layer switches is to create the network frame, which is high-speed switching of distribution switches. In most cases, the access layer switch is usually the last connection level, provided in this three-tiered connection architecture.
Q: What features should I look for in an access switch?
A: In the case of access switches, it is important to determine port density, Power over Ethernet (PoE) provision, the speed of a switch (e.g., a Gigabit PoE switch), security features, and management. The access layer switches within an enterprise should allow for the number of devices one wishes to connect and offer performance and features within the parameters of one’s network requirements.
Q: Are access switches Layer 3 switches?
A: Although access switches are mostly working within Layer 2 of the OSI model, newer models have more capabilities and act as Layer 3 switches. Layer 3 switches for your enterprise should provide additional routing functions within the access layer, which could be useful in certain design configurations. Nonetheless, in most circumstances, this access switch is the only Layer 2 switch in the network hierarchy.
Q: How many access switches do I need for my network?
A: The number of access switches needed depends on the size of your network and the number of devices that require connectivity. Systems that contain multiple switches tend to have sufficient port density and excess capacity. In addition, when deploying access switches, factors such as physical layout, number of end devices, and future expansion, which may enhance the need for more access switches, should be taken into account.
Q: What is the difference between a managed and an unmanaged access switch?
A: Managed access switches come with various options to configure them, thereby improving their use in the network. Unmanaged switches are easy-to-use, pre-assembled devices that are plug-and-play. In enterprise networks, managed switches are usually preferred since they have more advantages concerning security policy management.
Q: How do I ensure my access switches are secure?
A: When considering how best to secure your access switches, ensure you perform the following activities, among many others: changing default passwords, enabling port security, using VLAN access control lists (ACLs), and regularly updating switch firmware configuration. You might want to include these configurations as they help prevent attacks on the network system, such as DHCP and ARP attacks.
Q: Is it possible to stack or cluster access switches?
A: It is possible to stack or cluster various access switches. This type of management is useful as it treats all switches as a single logical unit for ease of management and redundancy purposes. Having a switch with stacking functionality is an advantage when enhancing the scalable design for network architecture because it makes it easy to expand your access layer with the growth of your network.
